In the digital age, seamless communication between devices is paramount. This is made possible by network protocols, the unsung heroes of the internet. But what is a protocol in the context of networking? Simply put, a network protocol is a standardized set of rules that govern how data is formatted, transmitted, and received across a network. These protocols allow diverse devices, from computers and servers to routers and virtual machines, to communicate effectively despite their differing hardware, software, and network architectures.
Without these protocols, the internet as we know it wouldn’t exist. Imagine a world where your computer couldn’t talk to a web server, or your email client couldn’t send messages. Network protocols provide the common language that enables these interactions, ensuring smooth and reliable communication for countless applications and services.
The OSI Model: A Framework for Understanding Network Protocols
To better understand What A Protocol Is and how it functions, it’s helpful to consider the Open Systems Interconnection (OSI) model. This conceptual model divides network communication into seven distinct layers, each with specific responsibilities and governed by one or more network protocols. This layered approach breaks down complex processes into manageable tasks, ensuring efficient and reliable data transfer.
Here’s a brief overview of the OSI model layers:
- Physical Layer: Deals with the physical transmission of data over a communication channel. This includes voltage levels, data rates, and physical connectors.
- Data Link Layer: Provides error-free transmission of data frames between two directly connected nodes. Protocols like Ethernet operate at this layer.
- Network Layer: Handles routing of data packets across a network. The Internet Protocol (IP) is a key protocol at this layer.
- Transport Layer: Provides reliable and ordered delivery of data between applications. TCP and UDP are common transport layer protocols.
- Session Layer: Manages the establishment, maintenance, and termination of sessions between applications.
- Presentation Layer: Handles data formatting, encryption, and decryption.
- Application Layer: Provides network services to applications, such as email, web browsing, and file transfer.
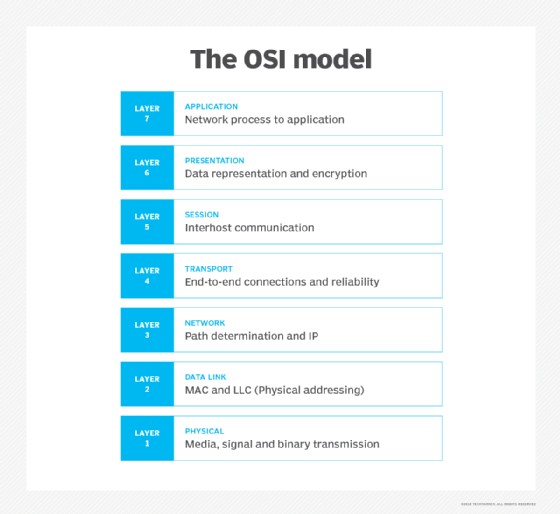 the OSI model
the OSI model
A diagram illustrating the seven layers of the OSI model, showing how applications communicate across a network.
Each layer in the OSI model relies on specific protocols to perform its functions. These protocols add headers and footers to data packets, containing information about the sender, receiver, and other relevant details. Network devices process these headers and footers to understand and route messages effectively.
The TCP/IP Model: The Internet’s Protocol Suite
While the OSI model is a valuable theoretical framework, the Transmission Control Protocol/Internet Protocol (TCP/IP) suite is the practical foundation of the internet. TCP/IP is a collection of protocols that work together to enable communication across networks. Unlike the OSI model, the TCP/IP suite consists of four layers:
- Link Layer: Responsible for data transmission over a physical link.
- Internet Layer: Handles routing of data packets between networks. IP is the primary protocol at this layer.
- Transport Layer: Provides reliable or unreliable data delivery between applications. TCP and UDP operate at this layer.
- Application Layer: Provides network services to applications. HTTP, FTP, SMTP, and DNS are examples of application layer protocols.
The TCP/IP model is the backbone of the internet, enabling countless applications and services to function seamlessly.
Types of Network Protocols
Network protocols can be broadly categorized into three types:
- Communication Protocols: These protocols define how data is exchanged between devices on a network. Examples include Ethernet, TCP, UDP, and HTTP.
- Management Protocols: These protocols are used to monitor, manage, and maintain network devices and services. SNMP and ICMP are examples of network management protocols.
- Security Protocols: These protocols provide security features such as encryption, authentication, and access control. Examples include SSL/TLS, SSH, and HTTPS.
Within these broad categories, thousands of specific network protocols exist, each designed to handle a particular task or function.
How Network Protocols Are Implemented
Network protocols are implemented in software and hardware. Operating systems and applications include built-in support for various network protocols. Additionally, dedicated hardware devices like routers and switches often implement specific protocols to optimize performance.
When a new protocol is introduced, it is typically added to a protocol suite, creating a layered architecture where protocols build upon each other.
Vulnerabilities of Network Protocols
While network protocols are essential for communication, they can also be vulnerable to security threats. Some protocols were not initially designed with security in mind, making them susceptible to attacks like eavesdropping, cache poisoning, and distributed denial-of-service (DDoS) attacks.
For example, a SYN flood attack exploits the TCP handshake process to overwhelm a server with connection requests, preventing legitimate users from accessing the service.
Network protocol analyzers and other security tools can help protect systems against these vulnerabilities by detecting and mitigating malicious activity.
Examples of Network Protocol Uses
Network protocols are used in a wide range of applications and services, including:
- Email: Protocols like SMTP (for sending email) and POP3/IMAP (for receiving email) enable email communication.
- File Transfer: FTP is used to transfer files between computers.
- Web Browsing: HTTPS secures communication between a web browser and a web server.
- Remote Access: Telnet allows users to connect to and control remote systems.
Here are some additional examples of network protocols:
- ARP (Address Resolution Protocol)
- BGP (Border Gateway Protocol)
- DHCP (Dynamic Host Configuration Protocol)
- DNS (Domain Name System)
- ICMP (Internet Control Message Protocol)
- OSPF (Open Shortest Path First)
- SSL/TLS (Secure Sockets Layer/Transport Layer Security)
- VoIP (Voice over IP)
Understanding what a protocol is is crucial for anyone working with networks or computers. They form the bedrock of all digital communication.
A visual representation of various network protocols at work.
By understanding the OSI model, TCP/IP suite, and the different types of network protocols, you can gain a deeper appreciation for the complex and interconnected world of networking. These protocols are constantly evolving to meet the demands of modern communication, ensuring that devices can continue to communicate seamlessly and securely.

