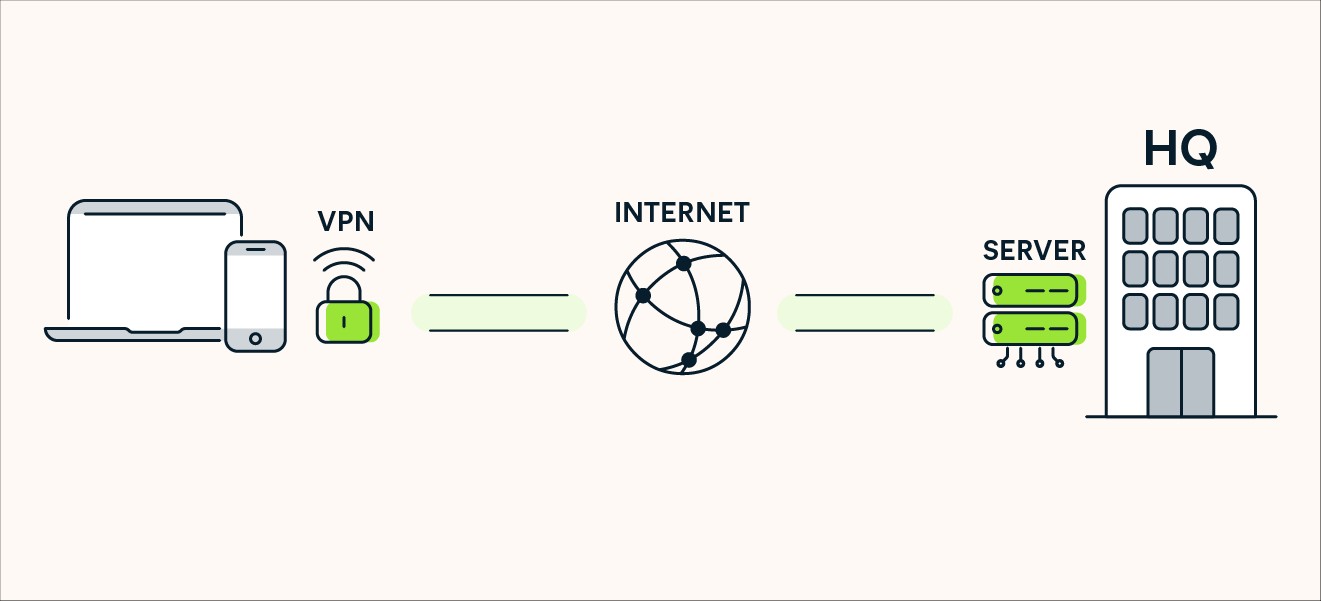
The acronym VPN stands for Virtual Private Network. But what does that really mean in practice? In essence, a VPN is a software tool or service that establishes a secure and encrypted connection between your device and the internet. Think of it as a digital shield that protects your online activities, ensuring privacy and security in an increasingly interconnected world.
Imagine the internet as a public street. Without a VPN, your online activities are like walking down that street in broad daylight – visible to anyone who happens to be watching. Your internet service provider (ISP), government agencies, and even cybercriminals could potentially monitor your browsing habits, track your location, and intercept your sensitive data.
A VPN acts as your personal, private tunnel on this public street. It encrypts your internet traffic, making it unreadable to prying eyes, and routes it through a remote server, masking your real IP address and location. This effectively makes you anonymous online, enhancing your privacy and security.
What Does a VPN Do?
A VPN’s core function is to create a secure, encrypted tunnel for your internet data. This tunnel acts as a protective barrier, safeguarding your information as it travels to and from your device. Let’s break down the key actions a VPN performs:
- Encrypts Your Internet Data: VPNs use advanced encryption algorithms to scramble your data, converting it into an unreadable format. This encryption ensures that even if someone intercepts your internet traffic, they won’t be able to decipher your sensitive information like passwords, emails, or financial details.
- Hides Your IP Address: Your IP (Internet Protocol) address is a unique identifier for your device on the internet, revealing your approximate location and ISP. A VPN masks your real IP address by routing your traffic through one of its servers. Websites and online services will see the VPN server’s IP address instead of yours, effectively hiding your identity and location.
- Bypasses Censorship and Surveillance: In regions with internet censorship or heavy government surveillance, VPNs can help you circumvent restrictions and access blocked content. By connecting to a VPN server in a different location, you can appear to be browsing from a country with fewer restrictions, granting you access to a wider range of information and online services.
- Accesses Geo-Blocked Content: Many streaming services, websites, and online content are geographically restricted, meaning they are only available in specific regions. VPNs allow you to bypass these geo-blocks by connecting to a server in the required location. For example, you can access US Netflix content from outside the US by connecting to a US-based VPN server.
- Avoids Bandwidth Throttling: Some ISPs intentionally slow down your internet speed (bandwidth throttling) when they detect bandwidth-intensive activities like streaming or downloading. By encrypting your traffic, a VPN can prevent your ISP from monitoring your online activities and throttling your bandwidth based on your usage.
- Enhances Security on Public Wi-Fi: Public Wi-Fi networks are often unsecured, making them vulnerable to hacking and eavesdropping. Using a VPN on public Wi-Fi creates a secure connection, protecting your data from potential threats while you are connected to these networks in cafes, airports, or hotels.
What Does a VPN Hide?
VPNs are powerful privacy tools, but it’s important to understand precisely what they conceal and what remains visible when you’re online. When you use a VPN, you effectively hide the following information:
- Your Location and IP Address: As mentioned, a VPN masks your real IP address and location, making it difficult for websites and trackers to pinpoint your geographic location.
- Your Browsing History from Your ISP: Your ISP can typically see your browsing history, including the websites you visit. A VPN encrypts your traffic, preventing your ISP from monitoring your online activities and the specific websites you access.
- Data You Send and Receive: All data transmitted through the VPN tunnel is encrypted. This includes emails, messages, downloaded files, and any other information you send or receive online, protecting it from interception.
- Files You Download: Your ISP can often see the types of files you download. With a VPN, this download activity is hidden from your ISP and other potential observers.
However, it’s crucial to note that VPNs do not anonymize everything. Certain online activities can still be tracked, even with a VPN enabled:
- Activity on Logged-In Sites: If you are logged into websites like social media platforms or email providers, your activity on these sites can still be tracked by those platforms, regardless of VPN usage.
- Cookies: Websites use cookies to track your browsing behavior. While a VPN hides your IP address, cookies stored in your browser can still be used to track your activity across different websites. Using a private browser or regularly clearing cookies can help mitigate this.
- Browser Fingerprinting: Advanced tracking techniques like browser fingerprinting can collect information about your browser and device configuration to create a unique “fingerprint” that can be used to identify you, even with a VPN.
- The Fact You’re Using a VPN: While VPNs hide your online activities, the fact that you are using a VPN might be detectable by websites or services, although your specific actions remain concealed.
To maximize your online privacy, combine VPN usage with other privacy-enhancing tools and practices, such as private browsers, secure messaging apps, and being mindful of the websites you log into and the information you share online.
Is a Virtual Private Network Safe to Use?
Generally, using a VPN is safe and a recommended practice for enhancing your online security and privacy. However, the safety of using a VPN heavily depends on choosing a reputable and trustworthy VPN provider.
Safe VPN Usage:
- Reputable Providers: Opt for established VPN providers with a proven track record of security and privacy. Look for providers with transparent privacy policies, positive user reviews, and independent audits of their security practices.
- Strong Encryption: Ensure the VPN uses strong encryption protocols, such as AES-256, to protect your data.
- No-Logs Policy: Choose a VPN provider that adheres to a strict no-logs policy, meaning they do not collect or store logs of your online activity, browsing history, or connection data.
- Essential Security Features: Features like a kill switch (which automatically disconnects your internet if the VPN connection drops) and DNS leak protection are crucial for maintaining consistent security.
Risks of Unsafe VPNs:
- Logging and Data Collection: Some free or less reputable VPN providers may log your online activity and sell your data to third parties for profit, directly contradicting the purpose of using a VPN for privacy.
- Malware and Security Vulnerabilities: Unsafe VPN apps can contain malware or have security vulnerabilities that expose your device to threats.
- Data Leaks: Poorly configured or insecure VPNs can suffer from data leaks, exposing your real IP address or DNS requests, undermining your anonymity.
- Slower Speeds and Poor Performance: Free or low-quality VPNs often have limited server infrastructure, resulting in slow speeds, unreliable connections, and a frustrating user experience.
While a VPN enhances your online security, it’s not a complete solution. You still need to practice safe online habits, be cautious about phishing attempts, and use robust antivirus software to protect against malware. Reputable VPNs like Avast SecureLine VPN offer bank-grade encryption, a no-logs policy, and additional security features to ensure a safe and private browsing experience.
[alt: Avast SecureLine VPN interface on desktop, showcasing server selection and connection status, emphasizing ease of use for secure browsing.]
How Does a VPN Work?
The technical process behind a VPN might seem complex, but the core functionality is straightforward. Here’s a simplified breakdown of how a VPN works:
- VPN Connection Establishment: You initiate a connection through your VPN client (app) on your device. You select a VPN server location from a list provided by your VPN service.
- Data Encryption: Once the connection is established, all internet traffic leaving your device is encrypted. This encryption process scrambles your data into an unreadable code, protecting it from eavesdropping.
- Data Encapsulation: Encrypted data is then encapsulated within additional data packets. This process further obscures the original data and adds another layer of security, making it harder to analyze or trace.
- Secure Tunneling: The encapsulated and encrypted data travels through a secure tunnel to the VPN server you selected. This tunnel acts as a private pathway, shielding your data from interception as it traverses the internet.
- Decryption and IP Address Masking at the VPN Server: When your data reaches the VPN server, it is decrypted. The VPN server then assigns you a new IP address, masking your real IP address. Your internet request is then forwarded to its destination (website, online service) as if it originated from the VPN server’s location.
- Return Path: When the website or online service sends data back to you, it first goes to the VPN server. The VPN server encrypts and encapsulates the data again, sending it back through the secure tunnel to your device, where it is decrypted and delivered to you.
How Do Encryption Tunnels Work?
VPNs utilize encryption tunnels to establish secure and private connections. These tunnels rely on cryptography, the art of secure communication, to protect data during transmission. Here’s a closer look at how encryption tunnels function:
- Cryptography: VPN tunnels use cryptographic protocols to convert your data into an unreadable format (ciphertext) before transmission and then back into its original form (plaintext) upon arrival at the destination.
- Encryption Keys: Encryption and decryption processes rely on encryption keys. These keys are complex algorithms that lock and unlock data. VPNs typically use strong encryption algorithms and key lengths to ensure robust security.
- Secure Pathways: Encryption tunnels create secure pathways for data transmission, preventing unauthorized access or interception. This pathway is established between your device and the VPN server, ensuring that all data exchanged within the tunnel remains private and secure.
- Data and Metadata Protection: Encryption tunnels not only protect the content of your data but also the metadata – information about the data, such as sender, receiver, and timestamps. This comprehensive protection enhances privacy and security.
Different VPN providers offer varying levels of encryption and utilize different cryptographic methods. Avast SecureLine VPN, for instance, employs 256-bit AES encryption, considered bank-grade and military-grade security. It combines hashing, symmetric cryptography, and asymmetric cryptography for a robust and multi-layered approach to data protection. Additionally, Avast employs its own DNS resolution system to further enhance security and prevent DNS-based tracking.
Is a VPN Worth It?
For most internet users, the answer is a resounding yes. The benefits of using a VPN for online privacy, security, and freedom of access often outweigh the minor drawbacks.
Benefits of Using a VPN:
- Enhanced Privacy: VPNs significantly enhance your online privacy by masking your IP address, encrypting your traffic, and preventing your ISP and other third parties from monitoring your browsing habits.
- Improved Security: VPNs secure your internet connection, especially on public Wi-Fi, protecting your data from hackers, cybercriminals, and surveillance.
- Access to Geo-Restricted Content: VPNs allow you to bypass geographical restrictions and access streaming services, websites, and content that might be blocked in your region.
- Bypass Censorship: In countries with internet censorship, VPNs can help you circumvent restrictions and access a free and open internet.
- Avoid Price Discrimination: VPNs can help you avoid price discrimination by masking your location, potentially leading to lower prices for online purchases, travel bookings, and other services.
- Prevent Bandwidth Throttling: VPNs can help you avoid bandwidth throttling by encrypting your traffic and preventing your ISP from monitoring your online activities.
[alt: Illustration depicting global streaming access with VPN, showing devices connecting to various international content platforms.]
Potential Negatives of Using a VPN:
- Slightly Slower Speeds: Encryption and routing traffic through VPN servers can sometimes slightly reduce your internet speed. However, reputable VPNs minimize this impact, and faster internet connections mitigate this concern.
- Cost: While there are free VPNs, they often come with limitations and security risks. Paid VPN services involve a subscription fee, but the cost is generally reasonable for the level of security and privacy they provide.
- VPN Blocking: Some websites or services attempt to block VPN usage. However, good VPN providers are adept at circumventing these blocks by constantly updating their servers and IP addresses.
- Not a Complete Privacy Solution: As mentioned earlier, VPNs are not a silver bullet for online privacy. They should be used in conjunction with other privacy-enhancing practices for comprehensive protection.
Overall: The advantages of using a VPN for enhancing privacy, security, and online freedom make it a valuable tool for anyone who values their digital safety and online experience. For a deeper understanding of the benefits, explore resources detailing the advantages of VPN usage in various scenarios.
Different Types of VPNs
VPN technology is versatile and can be implemented in various ways to suit different needs. Here are the primary types of VPNs you might encounter:
- Remote-Access VPNs: This is the most common type of VPN, designed for individual users. Remote-access VPNs allow you to connect your device (laptop, phone, tablet) to a private network or the public internet through an encrypted tunnel. This type is ideal for personal use, securing your home internet connection, or accessing your company’s network remotely.
- Site-to-Site VPNs (Router-to-Router VPNs): Primarily used in corporate environments, site-to-site VPNs connect entire networks in different locations. For example, a company with offices in multiple cities can use site-to-site VPNs to create a secure intranet, allowing employees in different locations to access shared resources as if they were on the same local network.
- Double VPNs: For users seeking an extra layer of security, Double VPNs route your internet traffic through two separate VPN servers. This encrypts your data twice, providing enhanced privacy and security but potentially impacting speed slightly.
- Specialty VPNs: Some VPN providers offer specialized VPN servers optimized for specific tasks, such as P2P VPN servers for file sharing, streaming VPN servers for optimized streaming performance, or Tor over VPN servers for added anonymity by combining VPN and Tor networks.
VPNs also differ in the VPN protocols they use. Protocols are sets of rules that govern how data is transmitted and secured through the VPN connection. Common VPN protocols include:
- OpenVPN: Widely considered one of the most secure and reliable protocols, open-source, and highly configurable.
- WireGuard: A newer protocol known for its speed and modern cryptography, offering a good balance of security and performance.
- IKEv2/IPSec: Fast and stable protocol, particularly good for mobile devices due to its ability to quickly re-establish connections when switching networks.
- L2TP/IPSec: Older protocol, generally considered less secure than OpenVPN or WireGuard but still used in some contexts.
- PPTP: Very old and now largely obsolete protocol, considered insecure and not recommended for use due to known vulnerabilities.
When choosing a VPN, consider the protocols offered and select one that balances security, speed, and compatibility with your devices and needs. Providers like Avast SecureLine VPN offer a range of secure protocols and allow you to choose the best option for your situation.
Do I Need a VPN?
In today’s digital landscape, a VPN is becoming increasingly essential for anyone who uses the internet. While not strictly mandatory, a VPN provides significant benefits that enhance your online experience and protect you from various threats.
Situations Where a VPN is Highly Recommended:
- Using Public Wi-Fi: Public Wi-Fi networks are inherently insecure. A VPN is crucial when using public Wi-Fi to protect your data from eavesdropping and hacking attempts.
- Online Banking and Shopping: VPNs secure your financial transactions and sensitive data when banking or shopping online, safeguarding your information from potential fraud and identity theft.
- Accessing Sensitive Information: When accessing confidential work documents, personal emails, or other sensitive data online, a VPN adds an essential layer of security.
- Streaming and Entertainment: If you want to access geo-restricted streaming content or avoid bandwidth throttling while streaming, a VPN is a valuable tool.
- Traveling: When traveling, you often rely on public Wi-Fi networks and may need to access content from your home country. A VPN ensures secure connections and access to your familiar online services.
- Gaming: VPNs can help prevent DDoS attacks in gaming, bypass regional restrictions, and potentially improve connection stability.
[alt: Person using a laptop in a cafe with a VPN icon overlay, highlighting VPN use on public Wi-Fi for security.]
Are VPNs Better Than Tor?
VPNs and Tor (The Onion Router) are both privacy tools, but they operate differently and offer different levels of anonymity and performance.
- VPNs: Provide a balance of strong encryption, good speeds, and ease of use. They are excellent for everyday privacy, security, and accessing geo-restricted content. VPNs encrypt your connection and route it through a single VPN server.
- Tor: Designed for maximum anonymity. Tor routes your internet traffic through a decentralized network of volunteer-run relays, making it very difficult to trace your online activity back to you. However, this multi-layered routing process significantly slows down internet speeds.
VPNs are generally better than Tor for:
- Speed and Performance: VPNs offer much faster speeds than Tor, making them suitable for streaming, downloading, and general browsing.
- Ease of Use: VPNs are user-friendly and easy to set up and use, while Tor can be more technically complex for some users.
- Everyday Privacy and Security: VPNs provide a strong level of privacy and security for daily online activities.
Tor might be preferred over VPNs for:
- Maximum Anonymity: If absolute anonymity is paramount, Tor offers a higher level of anonymity than VPNs due to its decentralized and multi-layered routing.
- Circumventing Extreme Censorship: In highly censored environments, Tor might be more effective at bypassing restrictions than VPNs in some cases.
In most common scenarios, a reputable VPN provides an excellent balance of privacy, security, speed, and usability, making it a more practical choice for the average user than Tor.
Can I Use a VPN on Any Device?
Yes, VPNs are compatible with a wide range of devices. Most reputable VPN providers offer apps and compatibility for various platforms, including:
- Computers: Windows, macOS, Linux
- Mobile Devices: Android, iOS (iPhone, iPad)
- Tablets: Android tablets, iPads
- Smart TVs and Streaming Devices: Some VPNs offer apps for certain smart TV platforms or can be configured on routers to protect all devices connected to the router.
- Routers: You can set up a VPN directly on your router to protect all devices connected to your home network, including IoT (Internet of Things) devices that may not support VPN apps directly.
Using a VPN on multiple devices is often possible with a single VPN subscription. For example, Avast SecureLine VPN allows you to connect up to ten devices simultaneously with one account, providing comprehensive protection for your entire digital life.
What to Look for When Choosing a VPN
Selecting the right VPN provider is crucial for ensuring effective privacy and security. Here are key factors to consider when choosing a VPN:
- Speed and Performance: Choose a VPN with fast server speeds and low latency to ensure smooth browsing, streaming, and downloading.
- Server Network: A large and geographically diverse server network provides more options for server locations, reduces server congestion, and improves reliability.
- Security and Encryption: Look for VPNs that use strong encryption protocols (AES-256) and offer essential security features like a kill switch and DNS leak protection.
- No-Logs Policy: A strict no-logs policy is paramount for privacy. Verify that the VPN provider does not log your browsing activity, connection data, or personal information.
- Reputation and Trustworthiness: Research the VPN provider’s reputation, read user reviews, and look for independent security audits to assess their trustworthiness.
- Ease of Use: Choose a VPN with user-friendly apps for your devices and a straightforward setup process.
- Customer Support: Reliable customer support, ideally 24/7, is essential for troubleshooting and assistance.
- Features: Consider additional features like simultaneous connections, split tunneling, ad-blocking, or specialized servers (e.g., P2P servers) based on your needs.
- Price: VPN prices vary. Compare pricing plans and consider the value offered in terms of features, performance, and security. Free trials are often available to test a service before committing to a subscription.
Should I Get a Free VPN?
While the idea of a free VPN is appealing, it’s generally advisable to avoid free VPN services for several reasons:
- Limited Security and Privacy: Free VPNs often have weaker security protocols, may log your data, and might not offer the same level of encryption as paid VPNs.
- Slow Speeds and Limited Bandwidth: Free VPNs typically have limited server resources, resulting in slow speeds, data caps, and a poor user experience.
- Intrusive Ads and Malware: Free VPN apps may bombard you with ads or even contain malware, compromising your security and privacy.
- Data Selling: Some free VPN providers may monetize their services by collecting and selling your data to third parties, undermining your privacy.
Opting for a reputable paid VPN service is a better investment for your online security and privacy. Paid VPNs offer robust security, faster speeds, reliable connections, and dedicated customer support. Many providers, including Avast SecureLine VPN, offer free trials, allowing you to experience the benefits of a premium VPN before subscribing.
History of VPNs — When Was the VPN Invented?
The concept of VPNs dates back to 1996, when a Microsoft employee, Gurdeep Singh-Pall, developed the Peer-to-Peer Tunneling Protocol (PPTP). Initially, VPN technology was primarily designed for corporate use, enabling remote employees to securely access company networks.
Consumer-level VPNs emerged later, around 2005, as internet users became increasingly concerned about online privacy and security. These consumer VPNs brought the benefits of secure and private network connections to individuals, allowing them to protect their online activities from prying eyes.
Since their inception, VPNs have evolved significantly. Protocols have become more secure and faster, server networks have expanded globally, and VPNs have become more user-friendly and accessible to a wider audience. Today, VPNs are a mainstream tool for online privacy and security, used by millions worldwide.
How Do I Set Up a VPN?
Setting up a VPN is typically a straightforward process, especially with user-friendly VPN apps. Here’s a general guide:
- Choose a VPN Provider: Select a reputable VPN provider that meets your needs and offers apps for your devices.
- Sign Up and Download the VPN App: Create an account with your chosen VPN provider and download their app for your operating system (Windows, macOS, Android, iOS, etc.).
- Install and Launch the VPN App: Install the VPN app on your device and launch it.
- Log In: Enter your VPN account credentials to log in to the app.
- Connect to a VPN Server: Select a server location from the list provided in the app (you can choose a server in your desired country). Click the “Connect” button to establish a VPN connection.
Once connected, your internet traffic will be routed through the VPN server, and your connection will be encrypted. To verify your VPN connection, you can use online IP address lookup tools to confirm that your IP address has changed to the VPN server’s IP address. Setting up Avast SecureLine VPN is particularly easy, with a one-click connection process.
Should I Leave My VPN On All the Time?
Leaving your VPN on all the time is generally a good practice for continuous online security and privacy. Benefits of Always-On VPN:
- Constant Protection: Ensures you are always protected, especially on unsecured networks.
- Privacy by Default: Makes privacy the default setting for your online activities.
- Peace of Mind: You don’t have to remember to turn on your VPN each time you connect to the internet.
Potential Drawbacks of Always-On VPN:
- Slight Speed Reduction: As mentioned, VPNs can sometimes slightly reduce internet speed.
- Battery Consumption: Running a VPN can consume a small amount of battery power on mobile devices.
- Occasional Website Compatibility Issues: Some websites or services might have limited functionality or block VPN connections, requiring you to temporarily disable the VPN for specific sites.
For most users, the benefits of always-on VPN outweigh the minor drawbacks. If you experience speed issues or website compatibility problems, you can temporarily disable the VPN as needed. However, for consistent security and privacy, keeping your VPN enabled is recommended.
Is My VPN Working?
To verify if your VPN is working correctly, you can check your IP address and location:
- Before Connecting to VPN: Go to a website like whatismyipaddress.com or iplocation.net. Note your IP address and location.
- Connect to Your VPN: Connect to your VPN server using your VPN app.
- After Connecting to VPN: Visit the same IP address lookup website again.
If your VPN is working correctly, you should see:
- A different IP address: The IP address displayed should be different from your original IP address and should match the IP address of the VPN server you connected to.
- A different location: The location displayed should correspond to the location of the VPN server you selected, not your real location.
These checks confirm that your IP address is masked and your internet traffic is being routed through the VPN server, indicating that your VPN is working as intended.
Use a Secure VPN Connection You Can Trust
Choosing a reliable VPN provider is paramount for your online security and privacy. Avast SecureLine VPN is a trusted option, offering robust security features, fast speeds, a global server network, and a strict no-logs policy. It’s designed for ease of use and provides a secure and private browsing experience across all your devices.
Take control of your online privacy and security today. Try Avast SecureLine VPN with a free trial and experience the benefits of a secure and reliable VPN connection.