In the world of computer networking, efficiency and organization are paramount. A subnet, short for subnetwork, is a fundamental concept that helps achieve both. Imagine a large city divided into distinct neighborhoods for better management and traffic flow. A subnet serves a similar purpose for computer networks, acting as a segmented piece of a larger network.
More technically, a subnet is a logical subdivision of an Internet Protocol (IP) network. It’s like taking a big IP network and breaking it down into multiple, smaller, and more manageable network segments. Organizations frequently use subnetting to logically group devices based on function, department, or location. This strategic division optimizes network traffic flow and enhances overall network performance. Each subnet operates with its own defined range of IP addresses, ensuring clear boundaries and efficient address allocation within the network.
Think of the postal service to understand the value of subnets. Just as city, state, and zip codes guide a letter through the postal system, subnets guide network traffic. Without this system, every post office would need to know every street address in the country. Subnets, like zip codes, allow routers (the network’s “post offices”) to efficiently direct data packets based on simple routing rules, significantly reducing unnecessary traffic and speeding up network communication. This segmentation, known as subnetting, is detailed in RFC 950 and is intrinsically linked to IP addresses, subnet masks, and CIDR notation.
How Subnets Function: The Technical Details
Subnets enable direct communication between devices within the same subnet. However, for devices in different subnets to communicate, routers are essential. Routers act as gateways, forwarding network traffic between subnets. Network administrators determine the size of each subnet, considering the network’s specific connectivity needs and the underlying network technology. Subnet size can vary dramatically, from point-to-point subnets connecting just two devices to expansive data center subnets designed to support thousands of connections.
Organizations have the autonomy to decide how many subnets to create and their sizes, constrained only by their allocated IP address space. The internal subnet structure of an organization remains localized and is not exposed to the outside network.
An IP address is fundamentally composed of two parts: the Network Prefix (or Network ID) and the Host ID. The delineation between these parts depends on the IP address class (A, B, or C).
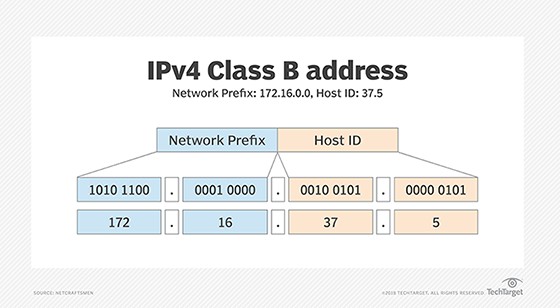
Figure 1. Class B IP address
Subnet ID and Host ID Explained
The subnet mechanism cleverly utilizes a portion of the Host ID field to identify individual subnets. Consider the Class B IP address 172.16.37.5 illustrated in Figure 1. Its Network Prefix is 172.16.0.0, and the Host ID is 37.5. Figure 2 demonstrates how the third group (octet) of the 172.16.0.0 network is used to designate the Subnet ID.
A crucial element in subnetting is the subnet mask. A subnet mask is used to pinpoint which part of the IP address functions as the Subnet ID. This is achieved through a binary AND operation applied to the IP address and the subnet mask. The AND operation, a fundamental concept in digital logic, yields a “true” (1) output only when both inputs are “true” (1). Otherwise, the output is “false” (0). In the context of subnetting, this operation isolates the Subnet ID.
Figure 2. Subnet ID
Figure 2 visually represents the AND operation between the IP address and the subnet mask, resulting in the Subnet ID. The remaining bits in the address then identify the Host ID within that subnet. In this example, the subnet is identified as 172.16.2.0, and the Host ID is 5. In practice, network administrators commonly refer to subnets simply by their Subnet ID. For instance, you might hear phrases like “Subnet 2 is experiencing issues today,” or “There’s a problem with the dot-two subnet.”
Routing Between Subnets
Routers leverage the Subnet ID to determine the optimal path for data transmission between subnetworks. Figure 3 depicts the 172.16.0.0 network, where the third octet is designated as the Subnet ID. It shows four of the 256 possible subnets connected to a single router. Each subnet is identified by its Subnet ID or the subnet address with the Host ID set to .0. Router interfaces are typically assigned a Host ID of .1, for example, 172.16.2.1.
When a router receives a data packet destined for a host on a different subnet (e.g., from host A to host C), it uses the subnet mask to identify the Subnet ID of host C. The router then consults its routing table to locate the interface connected to host C’s subnet and forwards the packet through that interface.
Subnet Segmentation: Further Division for Granular Control
The flexibility of subnetting extends further. A subnet itself can be further segmented into even smaller subnets. This hierarchical subnetting empowers organizations to create highly granular network divisions. This is particularly useful for scenarios like point-to-point links requiring minimal addresses or for creating subnetworks supporting a small number of devices with specific needs.
Figure 3. Subnet segmentation
The example in Figure 3 illustrates an 8-bit Subnet ID. The length of the subnet mask, determined by the number of bits allocated to the Subnet ID, is tailored to an organization’s specific requirements for subnet size and the desired number of subnets. While this adds a layer of complexity to network addressing, it significantly enhances the efficiency of IP address utilization.
A subnet can even be delegated to a sub-organization, which can then apply its own subnetting scheme to create further subnets, provided sufficient address space is available. This internal subnetting by a delegated organization remains hidden from the parent organization, a critical feature that enables networks to scale to enormous sizes without address conflicts or routing complexities.
Modern routing architectures employ routing protocols that distribute subnet masks along with routing information. These protocols also offer mechanisms to summarize groups of subnets into single routing table entries, simplifying routing management. Older routing systems relied on the default Class A, B, and C IP address classifications to infer the subnet mask, which was less flexible and efficient.
CIDR (Classless Inter-Domain Routing) notation, also known as Variable Length Subnet Masking (VLSM), is a standard method for representing network prefixes and subnet masks. For example, 172.16.2.0/24 uses “/24” to indicate that the first 24 bits of the IP address represent the network prefix, effectively defining the subnet mask. Subnetting principles and CIDR notation are applicable to both IPv4 and IPv6 networks.
This is an example of CIDR, which addresses the consistency of suffixes and prefixes that are meant to improve the efficiency of IP address distribution.
Consider a large global organization utilizing the 172.16.0.0/12 private address range. This allocation provides over a million private IP addresses (172.16.0.0 to 172.31.255.255). This vast address space can be further divided geographically. For example, the U.S. might be assigned 172.17.0.0/16, and Canada 172.18.0.0/16. These allocations can be further subdivided by building, floor, or department. If a device at 172.17.2.45 needs to communicate with 172.17.5.86, the router recognizes they are within the same building’s subnet and routes the traffic locally. However, if the same device at 172.17.2.45 needs to send data to 172.18.80.241, the router identifies that the destination is in a different geographical subnet (Canada) and forwards the traffic over the Wide Area Network (WAN) to the appropriate router in Canada.
Why Use Subnets? Benefits and Use Cases
Subnets are implemented for several key reasons, all contributing to improved network performance, manageability, and security:
- Efficient IP Address Reallocation: Traditional IP address classes (A, B, C) had fixed host allocations. Subnetting overcomes this limitation. For instance, a Class C network might be too small for an organization with more than 254 devices, while a Class B might be wasteful. Subnetting allows administrators to divide a larger address block into smaller, more appropriately sized subnets. This enables the efficient use of a single block of addresses across multiple physical networks, avoiding the need to request additional address blocks.
- Network Congestion Reduction: By segmenting a network into subnets, traffic is localized. Devices within a subnet primarily communicate with each other, reducing broadcast traffic and overall network congestion. Without subnets, every device on a large network would see all data packets, even if they were not the intended recipient. Subnets confine traffic, improving network speed and efficiency.
- Enhanced Routing Efficiency: Subnets provide valuable routing hints. Routers use subnet information to make intelligent forwarding decisions. Routing tables, which guide data traffic, become more efficient when networks are subnetted, leading to faster and more reliable data delivery.
Example of the contents of a routing table.
Subnetting and IP addressing are foundational elements of modern network infrastructure. Understanding these concepts is crucial for anyone involved in network administration or seeking a deeper understanding of how networks operate.
To further your understanding, explore how to calculate a subnet mask based on network requirements.