Edge computing is a distributed computing paradigm that brings computation and data storage closer to the sources of data. At WHAT.EDU.VN, we provide answers to your questions quickly and easily. Discover how it works, its benefits, and real-world applications. Learn about its relationship to cloud and fog computing and find out why it’s becoming increasingly important with our free consultation. Explore the future of distributed information technology with edge analytics and edge devices.
1. Understanding Edge Computing
Edge computing is a distributed information technology (IT) architecture where client data is processed at the network’s edge, near its originating source. Instead of sending vast amounts of raw data to a centralized data center or cloud for processing, edge computing performs computations closer to the data’s source.
This approach reduces latency, conserves bandwidth, and improves real-time decision-making capabilities.
1.1. The Evolution of Computing Paradigms
Traditional computing models relied on centralized data centers, which worked well for many business applications. However, the exponential growth of data generated by sensors, IoT devices, and other sources has strained these centralized systems. Bandwidth limitations, latency issues, and network disruptions can impede the efficient transfer and processing of this data.
Edge computing addresses these challenges by decentralizing processing power and bringing it closer to the data source. This shift in paradigm is crucial for applications that require real-time responses and low latency.
1.2. Key Characteristics of Edge Computing
- Proximity: Locating compute and storage resources near the data source.
- Decentralization: Distributing processing power away from centralized data centers.
- Real-time Processing: Enabling immediate analysis and decision-making.
- Bandwidth Conservation: Reducing the amount of data transmitted over the network.
- Autonomy: Operating independently, even with limited or intermittent connectivity.
1.3. Core Components of Edge Computing
Edge computing infrastructure typically involves the following components:
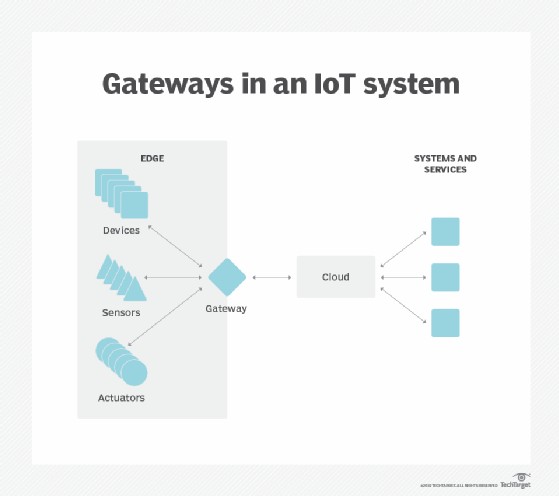
- Edge Devices: Sensors, IoT devices, and other endpoints that generate data.
- Edge Nodes: Computing resources (servers, gateways) located near the edge devices.
- Network Infrastructure: Communication links that connect edge devices and nodes.
- Management Platform: Tools for monitoring, managing, and securing the edge infrastructure.
1.4. Why Edge Computing Matters
Edge computing is becoming increasingly important because it addresses several critical challenges associated with modern data management:
- Reducing Latency: Minimizing delays in data processing and response times.
- Conserving Bandwidth: Decreasing the amount of data transmitted over networks.
- Improving Reliability: Ensuring continuous operation, even with network disruptions.
- Enhancing Security: Protecting sensitive data by processing it locally.
- Enabling New Applications: Supporting real-time analytics, AI, and automation at the edge.
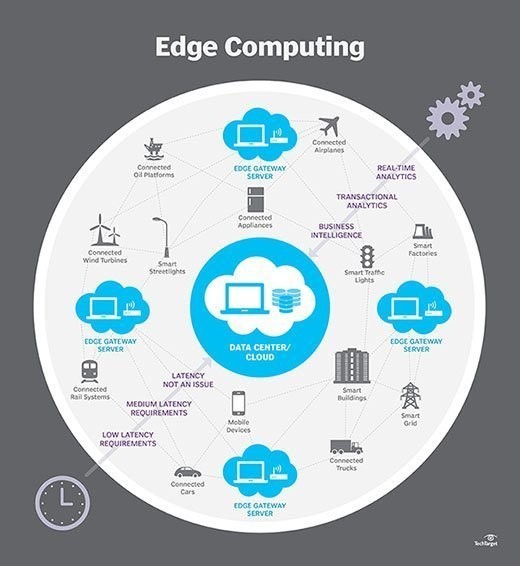
2. How Edge Computing Works
Edge computing operates by distributing computing and storage resources to the edge of the network, near the data sources. This approach contrasts with traditional centralized computing models, where data is transmitted to a central data center for processing.
2.1. Traditional Computing vs. Edge Computing
In a traditional computing model, data generated at a client endpoint (e.g., a user’s computer) travels across a wide area network (WAN) and a local area network (LAN) to a central data center. There, it is stored and processed by enterprise applications, and the results are sent back to the client endpoint.
However, this model is becoming less efficient as the volume of data generated by connected devices increases exponentially. Edge computing addresses this issue by moving storage and computing resources closer to the data source.
2.2. The Edge Computing Process
- Data Generation: Data is generated by edge devices, such as sensors, IoT devices, or user devices.
- Data Ingestion: The data is collected and ingested by edge nodes, which are typically located near the edge devices.
- Data Processing: The edge nodes perform data processing tasks, such as filtering, aggregation, and analysis.
- Decision-Making: Based on the processed data, real-time decisions are made at the edge.
- Data Transmission: Only essential data or insights are transmitted to the central data center or cloud for further analysis or archival.
2.3. Edge Nodes: The Workhorses of Edge Computing
Edge nodes are the computing resources that perform data processing tasks at the edge. These nodes can range from small, low-power devices to more powerful servers, depending on the specific application requirements.
Common types of edge nodes include:
- Gateways: Devices that connect edge devices to the network and perform basic data processing.
- Servers: More powerful computing resources that can handle complex data processing tasks.
- Micro Data Centers: Small, self-contained data centers that can be deployed at the edge.
2.4. Factors Influencing Edge Node Placement
The placement of edge nodes is a critical consideration in edge computing deployments. Factors that influence edge node placement include:
- Proximity to Data Source: Locating nodes as close as possible to the data source to minimize latency.
- Network Connectivity: Ensuring reliable network connectivity between edge nodes and the central data center.
- Environmental Conditions: Protecting nodes from harsh environmental conditions, such as extreme temperatures or moisture.
- Security Requirements: Implementing security measures to protect nodes from unauthorized access.
- Power Availability: Ensuring a reliable power supply for edge nodes.
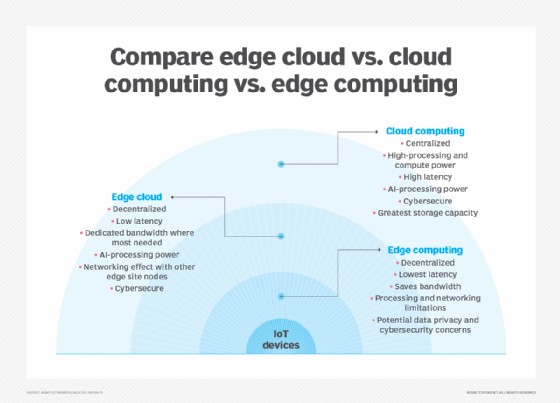
3. Edge vs. Cloud vs. Fog Computing
Edge computing is often associated with cloud computing and fog computing. Although these concepts share some similarities, they are distinct approaches to distributed computing.
3.1. Key Differences
| Feature | Edge Computing | Cloud Computing | Fog Computing |
|---|---|---|---|
| Location | At the edge of the network, near the data source | Centralized data centers | Between the edge and the cloud |
| Latency | Low | High | Moderate |
| Bandwidth | Conserves bandwidth | Requires high bandwidth | Reduces bandwidth requirements compared to cloud computing |
| Data Processing | Real-time processing | Batch processing | A mix of real-time and batch processing |
| Scalability | Limited scalability at the edge | High scalability | Moderate scalability |
| Use Cases | Real-time applications, autonomous systems | Data storage, large-scale analytics | Smart cities, industrial automation |
3.2. Cloud Computing
Cloud computing involves the deployment of computing and storage resources in centralized data centers, often located in different geographic regions. Cloud providers offer a wide range of services, including:
- Infrastructure as a Service (IaaS): Provides virtualized computing resources over the internet.
- Platform as a Service (PaaS): Offers a platform for developing and deploying applications.
- Software as a Service (SaaS): Delivers software applications over the internet.
While cloud computing offers scalability and cost-effectiveness, it can introduce latency and bandwidth limitations for applications that require real-time responses.
3.3. Fog Computing
Fog computing is an intermediate layer between edge and cloud computing. It involves deploying computing and storage resources closer to the edge than the cloud, but not directly at the edge.
Fog computing is often used in scenarios where edge computing is impractical due to resource constraints or geographic distribution. It enables data processing and analysis to be performed closer to the data source than the cloud, but with more resources than edge computing.
3.4. Complementary Technologies
Edge, cloud, and fog computing are not mutually exclusive. They can be used together to create a comprehensive distributed computing architecture. For example, edge computing can be used for real-time processing, while cloud computing can be used for long-term data storage and analysis.
4. Why Is Edge Computing Important?
Edge computing is important because it addresses several critical limitations of traditional centralized computing models, particularly in the context of the Internet of Things (IoT) and real-time applications.
4.1. Overcoming Network Limitations
- Bandwidth: Edge computing reduces the amount of data transmitted over the network, conserving bandwidth and reducing costs.
- Latency: By processing data closer to the source, edge computing minimizes latency, enabling real-time responses.
- Congestion: Edge computing alleviates network congestion by distributing processing power and reducing the load on central data centers.
- Reliability: Edge computing improves reliability by enabling applications to continue operating even when network connectivity is limited or disrupted.
4.2. Supporting Real-Time Applications
Many modern applications require real-time processing and decision-making. Edge computing enables these applications by providing low-latency access to data and computing resources.
Examples of real-time applications that benefit from edge computing include:
- Autonomous Vehicles: Edge computing enables vehicles to process sensor data and make real-time decisions about navigation and safety.
- Industrial Automation: Edge computing enables factories to monitor and control equipment in real-time, improving efficiency and reducing downtime.
- Healthcare Monitoring: Edge computing enables healthcare providers to monitor patients remotely and respond to critical events in real-time.
- Smart Cities: Edge computing enables cities to monitor and manage infrastructure, traffic, and public safety in real-time.
4.3. Enabling New Business Models
Edge computing is enabling new business models by providing organizations with the ability to collect, process, and analyze data in new ways. For example, edge computing can be used to:
- Improve Customer Experiences: By providing real-time personalized experiences based on customer data.
- Optimize Operations: By monitoring and controlling equipment and processes in real-time.
- Develop New Products and Services: By using edge computing to collect and analyze data from new sources.
5. Edge Computing Use Cases and Examples
Edge computing is being used in a wide range of industries and applications. Here are some notable examples:
5.1. Manufacturing
In manufacturing, edge computing is used to monitor production processes, detect defects, and improve product quality. By deploying sensors and edge nodes throughout the factory floor, manufacturers can collect and analyze data in real-time, enabling them to make faster and more accurate decisions.
Example: A manufacturer uses edge computing to monitor environmental conditions throughout the plant, providing insights into how each product component is assembled and stored, and how long components remain in stock.
5.2. Agriculture
Edge computing is transforming agriculture by enabling farmers to monitor crops, optimize irrigation, and reduce pesticide use. By deploying sensors and edge nodes in the field, farmers can collect and analyze data about soil conditions, weather patterns, and crop health.
Example: A business grows crops indoors without sunlight, soil, or pesticides, reducing grow times by more than 60%. Sensors track water use and nutrient density to determine optimal harvest times.
5.3. Retail
Retail businesses are using edge computing to improve customer experiences, optimize inventory management, and prevent theft. By deploying cameras, sensors, and edge nodes in stores, retailers can collect and analyze data about customer behavior, product demand, and security threats.
Example: Retailers use video surveillance and sales data to determine optimal product configurations and predict consumer demand.
5.4. Healthcare
Edge computing is revolutionizing healthcare by enabling remote patient monitoring, real-time diagnostics, and personalized treatment. By deploying sensors, wearables, and edge nodes in hospitals and homes, healthcare providers can collect and analyze data about patient health, enabling them to provide more timely and effective care.
Example: The healthcare industry applies automation and machine learning to patient data collected from devices, sensors, and other medical equipment, enabling clinicians to take immediate action to help patients avoid health incidents in real time.
5.5. Transportation
In the transportation industry, edge computing is used to enable autonomous vehicles, optimize traffic flow, and improve safety. By deploying sensors, cameras, and edge nodes in vehicles and infrastructure, transportation providers can collect and analyze data about vehicle performance, road conditions, and traffic patterns.
Example: Autonomous vehicles use onboard computing to aggregate and analyze data about location, speed, vehicle condition, road conditions, and traffic conditions in real time.
5.6. Workplace Safety
Edge computing can combine and analyze data from on-site cameras, employee safety devices, and various other sensors to help businesses oversee workplace conditions or ensure that employees follow established safety protocols — especially when the workplace is remote or unusually dangerous, such as construction sites or oil rigs.
6. Benefits of Edge Computing
Edge computing offers numerous benefits across various industries and applications. These benefits can be broadly categorized as follows:
6.1. Improved Performance
- Reduced Latency: Edge computing minimizes delays in data processing and response times, enabling real-time applications.
- Increased Bandwidth: By processing data locally, edge computing reduces the amount of data transmitted over the network, conserving bandwidth.
- Enhanced Reliability: Edge computing enables applications to continue operating even when network connectivity is limited or disrupted.
6.2. Enhanced Security
- Data Sovereignty: Edge computing enables organizations to keep data within their own jurisdiction, complying with data privacy regulations.
- Reduced Attack Surface: By processing data locally, edge computing reduces the attack surface and protects sensitive data from unauthorized access.
- Improved Compliance: Edge computing helps organizations comply with industry-specific regulations, such as HIPAA in healthcare and PCI DSS in finance.
6.3. Cost Savings
- Reduced Bandwidth Costs: Edge computing reduces the amount of data transmitted over the network, lowering bandwidth costs.
- Optimized Infrastructure: Edge computing enables organizations to optimize their infrastructure by deploying computing resources only where they are needed.
- Improved Efficiency: By enabling real-time monitoring and control, edge computing improves operational efficiency and reduces downtime.
6.4. Autonomy
Edge computing is useful where connectivity is unreliable or bandwidth is restricted because of the site’s environmental characteristics. Examples include oil rigs, ships at sea, remote farms, or other remote locations, such as a rainforest or desert. Edge computing does the compute work on-site — sometimes on the edge device itself — such as water quality sensors on water purifiers in remote villages, and can save data to transmit to a central point only when connectivity is available. By processing data locally, the amount of data to be sent can be vastly reduced, requiring far less bandwidth or connectivity time than might otherwise be necessary.
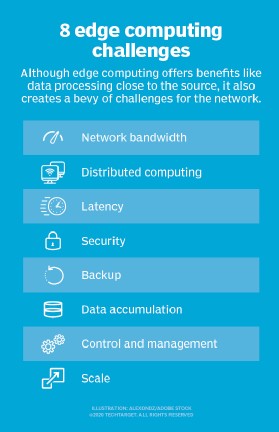
7. Challenges of Edge Computing
Despite its numerous benefits, edge computing also presents several challenges that organizations must address:
7.1. Limited Resources
- Compute Power: Edge nodes typically have limited compute power compared to centralized data centers.
- Storage Capacity: Edge nodes have limited storage capacity, requiring organizations to carefully manage data storage.
- Network Bandwidth: Edge nodes may have limited network bandwidth, requiring organizations to optimize data transmission.
7.2. Security Risks
- Physical Security: Edge nodes are often deployed in remote or unattended locations, making them vulnerable to physical theft or damage.
- Cybersecurity Threats: Edge nodes are susceptible to cybersecurity threats, such as malware and hacking.
- Data Breaches: Data stored on edge nodes can be vulnerable to data breaches if not properly secured.
7.3. Management Complexity
- Remote Management: Edge nodes are often deployed in remote locations, making them difficult to manage and maintain.
- Scalability: Scaling edge computing deployments can be complex and challenging.
- Integration: Integrating edge computing with existing IT infrastructure can be complex and time-consuming.
7.4. Connectivity
Edge computing overcomes typical network limitations, but even the most forgiving edge deployment will require some minimum level of connectivity. It’s critical to design an edge deployment that accommodates poor or erratic connectivity and consider what happens at the edge when connectivity is lost. Autonomy, AI, and graceful failure planning in the wake of connectivity problems are essential to successful edge computing.
8. Edge Computing Implementation
Implementing edge computing requires a strategic approach that considers the organization’s specific needs and challenges. Here are some key steps:
8.1. Define Business Goals
Start by defining the business goals that you want to achieve with edge computing. This will help you determine the appropriate use cases and deployment strategy.
8.2. Assess Technical Requirements
Assess your technical requirements, including compute power, storage capacity, network bandwidth, and security needs.
8.3. Choose the Right Architecture
Select the right edge computing architecture based on your business goals and technical requirements.
8.4. Select Hardware and Software
Choose hardware and software components that are compatible with your chosen architecture and meet your performance, security, and management requirements.
8.5. Deploy and Manage Edge Nodes
Deploy and manage edge nodes in accordance with your chosen architecture and security policies.
8.6. Monitor and Optimize Performance
Monitor and optimize the performance of your edge computing deployment to ensure that it meets your business goals.
8.7. Edge Maintenance
- Security. Physical and logical security precautions are vital and should involve tools that emphasize vulnerability management and intrusion detection and prevention. Security must extend to sensor and IoT devices, as every device is a network element that can be accessed or hacked — presenting a bewildering number of possible attack surfaces.
- Connectivity. Connectivity is another issue, and provisions must be made for access to control and reporting even when connectivity for the actual data is unavailable. Some edge deployments use a secondary connection for backup connectivity and control.
- Management. The remote and often inhospitable locations of edge deployments make remote provisioning and management essential. IT managers must be able to see what’s happening at the edge and be able to control the deployment when necessary.
- Physical maintenance. Physical maintenance requirements can’t be overlooked. IoT devices often have limited lifespans with routine battery and device replacements. Gear fails and eventually requires maintenance and replacement. Practical site logistics must be included with maintenance.
9. The Future of Edge Computing
Edge computing is a rapidly evolving field, with new technologies and applications emerging all the time. Here are some key trends shaping the future of edge computing:
9.1. Integration with 5G
5G wireless technology is expected to accelerate the adoption of edge computing by providing faster and more reliable network connectivity. 5G will enable new applications that require low latency and high bandwidth, such as autonomous vehicles and virtual reality.
9.2. Artificial Intelligence at the Edge
Artificial intelligence (AI) is increasingly being deployed at the edge, enabling real-time data analysis and decision-making. AI at the edge can be used to improve performance, enhance security, and automate tasks.
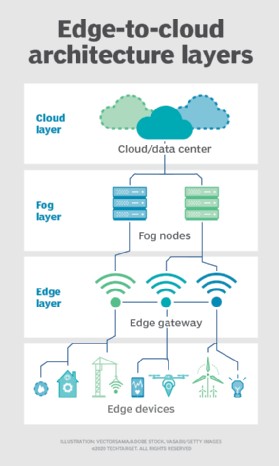
9.3. Edge-to-Cloud Continuum
The edge-to-cloud continuum is a model that seamlessly integrates edge computing with cloud computing. This model enables organizations to leverage the benefits of both edge and cloud computing, providing a flexible and scalable platform for data processing and analysis.
9.4. Micro Modular Data Centers (MMDCs)
The MMDC is basically a data center in a box, putting a complete data center within a small mobile system that can be deployed closer to data — such as across a city or a region — to get computing much closer to data without putting the edge at the data proper.
10. Frequently Asked Questions (FAQs) About Edge Computing
| Question | Answer | Source |
|---|---|---|
| What Is Edge Computing, in simple terms? | Edge computing is like having mini-data centers located closer to where data is collected, allowing faster processing and reducing the need to send everything to a central server. | N/A |
| How does edge computing differ from cloud computing? | Cloud computing involves centralized data centers, while edge computing distributes processing to the network’s edge. | Edge vs. Cloud vs. Fog Computing |
| What are the primary benefits of edge computing? | Reduced latency, bandwidth conservation, enhanced security, and improved reliability. | Benefits of Edge Computing |
| What are some common use cases for edge computing? | Manufacturing, agriculture, retail, healthcare, and transportation. | Edge Computing Use Cases and Examples |
| What are the challenges associated with edge computing? | Limited resources, security risks, and management complexity. | Challenges of Edge Computing |
| How does 5G technology impact edge computing? | 5G provides faster and more reliable network connectivity, accelerating the adoption of edge computing. | The Future of Edge Computing |
| What is the role of AI in edge computing? | AI enables real-time data analysis and decision-making at the edge, improving performance and automation. | The Future of Edge Computing |
| How do I get started with edge computing? | Define business goals, assess technical requirements, choose the right architecture, and select hardware and software. | Edge Computing Implementation |
| What is the edge-to-cloud continuum? | A model that seamlessly integrates edge computing with cloud computing for flexible data processing. | The Future of Edge Computing |
| Where can I find reliable information about edge computing? | WHAT.EDU.VN offers comprehensive resources and free consultations to answer your questions about edge computing. | WHAT.EDU.VN |
Unlock the Power of Edge Computing with WHAT.EDU.VN
Do you have more questions about edge computing and how it can transform your business? Are you struggling to find reliable and free answers? Look no further. At WHAT.EDU.VN, we provide expert insights and free consultations to help you navigate the complexities of edge computing.
Don’t let bandwidth limitations, latency issues, or security concerns hold you back. Contact us today and discover how edge computing can revolutionize your operations.
Address: 888 Question City Plaza, Seattle, WA 98101, United States
WhatsApp: +1 (206) 555-7890
Website: WHAT.EDU.VN
Visit what.edu.vn now to ask your questions and receive expert guidance on edge computing and other cutting-edge technologies – all for free. Your answers are just a click away.
