Kerberos authentication is a network security protocol that verifies user and service identities, bolstering network security. At WHAT.EDU.VN, we provide simple answers to complex questions, clarifying concepts like network authentication, identity management, and security protocols. Discover Kerberos, and ask any question on WHAT.EDU.VN for free to learn more about network security or authentication systems.
1. Understanding the Basics of Kerberos
Kerberos is like a digital gatekeeper for your network. But what does that mean for you? Let’s break it down.
1.1 What is Kerberos and How Does It Function?
Kerberos is an authentication protocol that allows trusted hosts to exchange information securely across an untrusted network, like the internet. It acts as a secure gateway, verifying the identities of users and services to prevent unauthorized access. It uses secret key cryptography, also known as symmetric key cryptography, to ensure secure communication.
1.2 What Are the Core Components of Kerberos?
Kerberos has three main components, inspired by the mythical three-headed dog Cerberus:
- Client/Principal: The user or system requesting access.
- Network Resource: The server hosting the resource.
- Key Distribution Center (KDC): The trusted server that manages authentication.
The KDC includes:
- Authentication Server (AS): Handles initial authentication.
- Ticket-Granting Server (TGS): Issues service tickets.
- Database: Stores user details for verification.
1.3 Why is Kerberos Important for Network Security?
Kerberos plays a vital role in maintaining the authentication, authorization, and accounting (AAA) triad in network security by ensuring that only verified users and services can access sensitive data.
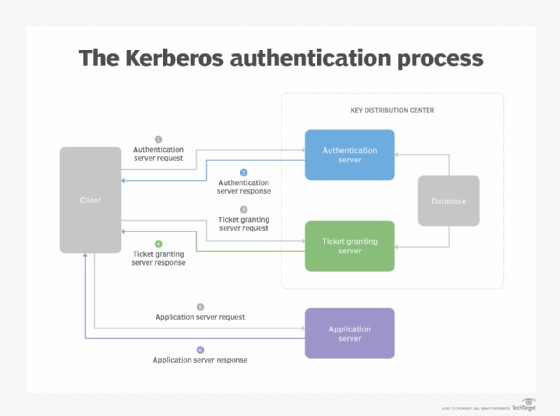
2. How Kerberos Authentication Works: A Step-by-Step Guide
Understanding the Kerberos process is essential for grasping its security benefits.
2.1 The Kerberos Authentication Process
The Kerberos authentication process involves a series of steps to ensure secure access:
- Authentication Request (AS Request): The client sends a plaintext authentication request to the KDC’s AS.
- Authentication Response (AS Response): The AS verifies the client’s credentials against its database and sends a Ticket Granting Ticket (TGT) and session key back to the client.
- Service Ticket Request: The client requests a service ticket from the TGS using the TGT.
- Service Ticket Response: The TGS authenticates the client and sends a service ticket encrypted with a session key.
- Application Server Request: The client sends the service ticket to the application server to request access.
- Application Server Response (Optional): The application server authenticates itself back to the client.
2.2 What is a Kerberos Ticket and Why is it Important?
A Kerberos ticket is a timestamped credential that allows a client to access a specific service without re-authenticating. The limited validity period of tickets reduces the risk of unauthorized use by attackers.
2.3 How Does Kerberos Ensure Secure Communication?
Kerberos ensures secure communication through symmetric key cryptography, which encrypts messages between the client and server. This prevents eavesdropping and tampering.
 Flow chart showing how a user request leads to authentication and approved access
Flow chart showing how a user request leads to authentication and approved access
3. The Advantages of Using Kerberos Authentication
Kerberos offers several benefits that make it a preferred choice for network authentication.
3.1 What Are the Key Benefits of Kerberos?
- Centralized Authentication: Kerberos uses a central KDC, reducing the need to trust individual servers.
- Strong Cryptography: It uses symmetric key cryptography to protect data.
- Protection Against Attacks: Kerberos prevents eavesdropping and replay attacks.
- Effective Access Control: Administrators can enforce security policies centrally.
- Improved User Experience: Single sign-on (SSO) capabilities minimize the need for repeated logins.
3.2 How Does Kerberos Improve User Experience?
Kerberos improves user experience by enabling single sign-on (SSO), where users only need to authenticate once to access multiple services. This streamlines the login process and enhances productivity.
3.3 How Does Kerberos Enhance Network Security?
Kerberos enhances network security by ensuring that passwords are never transmitted over the network and are not stored in plaintext, even on the AS. This minimizes the risk of password theft and unauthorized access.
4. Objectives, Concepts, and Terms in Kerberos
To fully understand Kerberos, it’s important to grasp its underlying principles and vocabulary.
4.1 What Are the Primary Objectives of Kerberos?
- Never transmit passwords over the network.
- Avoid storing passwords on client systems.
- Never store passwords in plaintext, even on authentication servers.
- Require users to enter their password only once per session (SSO).
- Maintain all authentication information in a centralized authentication server.
- Ensure all parties (users and application servers) authenticate themselves.
- Provide a mechanism for clients and servers to set up encrypted communication channels.
4.2 Key Concepts and Terminology in Kerberos
Familiarizing yourself with key terms will aid your understanding:
| Term | Definition |
|---|---|
| Principal | A unique identity to which Kerberos can assign tickets (e.g., user ID, host, service). |
| Realm | A network region in which Kerberos servers operate, identified by a domain name. |
| Authentication Ticket | A credential indicating that a user has been authenticated through the Kerberos authentication service. |
| Session Key | A temporary cryptographic key used for secure communication between a client and a server. |
| Ticket Granting Ticket (TGT) | A credential used to obtain service tickets. |
4.3 How Does Kerberos Achieve Single Sign-On (SSO)?
Kerberos achieves SSO by issuing a TGT after the initial authentication, which allows users to access other services without re-entering their credentials. This simplifies access management and improves security.
5. A Brief History of Kerberos
Knowing the origins of Kerberos can provide context for its current usage and relevance.
5.1 The Origins of Kerberos at MIT
Kerberos was developed at MIT in the 1980s as part of Project Athena, which aimed to provide easier access to computing resources for students. The protocol was designed to secure network authentication in an environment where traditional methods were vulnerable to eavesdropping.
5.2 How Did Kerberos Evolve Over Time?
Initially named the Kerberos Authentication and Authorization System, Kerberos was created to provide a secure way for users to authenticate themselves and access network resources. It has since been adopted by numerous operating systems and is now an integral part of many secure systems.
5.3 Current Implementations and Versions of Kerberos
The current version of Kerberos, as of March 2025, is V5 Release 1.21.3, which includes fixes for vulnerabilities and improvements in performance. It is widely used in operating systems like Microsoft Windows and is supported by cloud platforms like Amazon Web Services (AWS) and Google Cloud.
6. Common Uses of Kerberos Today
Kerberos is employed in a variety of systems to ensure secure authentication and access control.
6.1 Where is Kerberos Commonly Used?
Kerberos is used in:
- Cloud Computing Platforms: Amazon Web Services (AWS), Google Cloud, Microsoft Azure.
- Operating Systems: Apple macOS, Hewlett Packard Unix, IBM Advanced Interactive eXecutive, Microsoft Windows Server, Oracle Solaris, Red Hat Enterprise Linux, FreeBSD, and OpenBSD.
- Directory Services: Microsoft Active Directory (AD).
6.2 Kerberos in Cloud Computing
Cloud platforms use Kerberos to manage access to various services and resources, ensuring that only authenticated and authorized users can access sensitive data.
6.3 Kerberos in Operating Systems
Many operating systems incorporate Kerberos for user authentication, providing a secure and reliable method for verifying user identities. For example, Microsoft Windows uses Kerberos V5 as its default authentication method.
7. Security Aspects of Kerberos
Kerberos is generally considered secure, but it’s important to stay informed about potential vulnerabilities and how to mitigate them.
7.1 How Secure is Kerberos?
Kerberos is a secure and mature authentication mechanism that uses strong cryptography to protect sensitive data and limit resource access to authenticated and authorized users.
7.2 Common Security Weaknesses and Attacks on Kerberos
- Pass-the-Key Attack: Attackers impersonate authorized users by replaying their credentials.
- Pass-the-Ticket Attack: Attackers intercept and reuse tickets.
- Golden Ticket Attack: Attackers gain access to the domain controller to create credentials with unlimited access.
7.3 How to Keep Kerberos Secure
To maintain Kerberos security:
- Stay updated on security vulnerabilities.
- Implement all software updates.
- Monitor network activity for suspicious behavior.
- Enforce strong password policies.
8. Kerberos Compared to Other Network Authentication Protocols
Understanding how Kerberos stacks up against other protocols can help you choose the right solution for your needs.
8.1 Kerberos vs. Microsoft NTLM
Microsoft NTLM is an authentication protocol used in Windows environments that employs a challenge-response mechanism. However, Microsoft prefers Kerberos V5 for Active Directory environments due to its enhanced security features.
8.2 Kerberos vs. LDAP
LDAP (Lightweight Directory Access Protocol) is a directory access protocol used for connecting to and searching internet directories. While Kerberos provides authentication, LDAP provides authorization services. Often, they are used together for comprehensive network security.
8.3 Kerberos vs. RADIUS
RADIUS (Remote Authentication Dial-In User Service) is used for authenticating dial-in users remotely. It can be integrated with Kerberos for stronger authentication and can also handle authorization and accounting of network services.
9. Key Entities in Kerberos
Knowing the entities that interact within Kerberos helps clarify the authentication process.
9.1 What is a Kerberos Principal?
A Kerberos principal is a unique identity to which Kerberos can assign a ticket, such as a user ID, host, or service. It is uniquely identified by a primary name, an optional identifier, and a realm.
9.2 The Role of the Kerberos Application Server
The Kerberos application server provides access to resources and requires client authentication through Kerberos. These can include file and print services, terminal emulation, remote computing, and email.
9.3 Components of the Kerberos Key Distribution Center (KDC)
The KDC includes:
- Kerberos Database: Maintains records for each principal in the realm.
- Kerberos Authentication Service: Authenticates clients to get a TGT.
- Kerberos Ticket-Granting Service: Issues service tickets to access application servers.
10. Frequently Asked Questions (FAQ) About Kerberos
Answering common questions can further clarify your understanding of Kerberos.
10.1 General Questions
| Question | Answer |
|---|---|
| What is the main purpose of Kerberos? | To provide secure authentication for client-server applications by using secret-key cryptography. |
| How does Kerberos prevent password theft? | By never transmitting passwords over the network and avoiding their storage in plaintext. |
| What is a Kerberos realm? | A network region in which Kerberos servers operate, identified by a domain name. |
| Can Kerberos be used with cloud services? | Yes, many cloud platforms like AWS, Google Cloud, and Azure support Kerberos for secure access management. |
| What are the limitations of Kerberos? | Requires a trusted KDC, can be complex to configure, and is vulnerable to certain types of attacks if not properly maintained. |
10.2 Technical Questions
| Question | Answer |
|---|---|
| What is the difference between a TGT and a service ticket? | A TGT is used to obtain service tickets, while a service ticket is used to access specific application services. |
| How does Kerberos handle encryption? | By using symmetric key cryptography to encrypt messages between clients and servers, ensuring secure communication. |
| What are the steps for setting up Kerberos authentication? | Install and configure the KDC, create principals for users and services, and configure client applications to use Kerberos for authentication. |
| How do you troubleshoot Kerberos authentication issues? | Check KDC configuration, verify principal settings, review network connectivity, and analyze Kerberos logs for errors. |
| What are the common Kerberos error codes and their meanings? | KDC_ERR_S_PRINCIPAL_UNKNOWN (principal not found), KDC_ERR_PREAUTH_REQUIRED (pre-authentication required), KRB_AP_ERR_TKT_EXPIRED (ticket has expired). |
10.3 Security Questions
| Question | Answer |
|---|---|
| How does Kerberos protect against replay attacks? | By including timestamps in tickets and validating them at the server, ensuring that tickets cannot be reused outside their validity period. |
| What is the impact of a compromised KDC? | A compromised KDC can lead to unauthorized access to all Kerberos-protected resources, making it critical to secure the KDC and regularly audit its operations. |
| How does Kerberos handle password changes? | When a user changes their password, the KDC updates the principal’s key, and the user needs to obtain a new TGT to continue accessing services. |
| What are the best practices for securing a Kerberos realm? | Use strong encryption algorithms, regularly update Kerberos software, monitor the KDC for intrusions, and implement strict access control policies. |
| How can you detect a pass-the-ticket attack in Kerberos? | Monitor network traffic for unusual ticket requests, analyze authentication logs for suspicious activity, and implement intrusion detection systems to identify and block such attacks. |
Have more questions about Kerberos or network security? Visit WHAT.EDU.VN to ask your questions and get free answers from our experts.
Conclusion: Simplifying Kerberos Authentication
Kerberos is a robust authentication protocol that enhances network security by verifying user and service identities. Understanding its components, processes, and benefits can help you appreciate its role in modern computing environments. At WHAT.EDU.VN, we are dedicated to providing clear and concise explanations to help you grasp complex topics easily. Do you have any questions? Ask them now for free at WHAT.EDU.VN.
Address: 888 Question City Plaza, Seattle, WA 98101, United States.
Whatsapp: +1 (206) 555-7890.
Website: what.edu.vn
Don’t hesitate to reach out and discover the answers you’re looking for!
