You’ve likely encountered scenarios where a website or app requests access to your data on another platform, like allowing a service to post on your behalf on social media. Instead of sharing your password, a secure protocol called OAuth is used. But What Is Oauth, and how does it work? This guide breaks down OAuth, its benefits, and how it ensures secure delegated access.
Understanding OAuth: Secure Delegated Access
OAuth (Open Authorization) is an open-standard authorization framework that enables applications to obtain “secure delegated access” to user resources. Imagine granting ESPN.com permission to access your Facebook profile or post updates without revealing your Facebook password. This is the power of OAuth. If ESPN experiences a security breach, your Facebook password remains protected.
OAuth achieves this by using authorization tokens instead of sharing password data. It acts as an intermediary, allowing one application to interact with another on your behalf without compromising your credentials. This approach minimizes risks associated with sharing sensitive information.
 OAuth Explained
OAuth Explained
Alternative text: Diagram illustrating the OAuth process, showing the interaction between user, consumer application, and service provider to grant access without sharing credentials.
OAuth vs. SAML: Key Differences
Another federated authentication standard, SAML (Security Assertion Markup Language), is often used by enterprises for Single-Sign-On (SSO). SAML helps organizations monitor access to corporate resources. While both address authentication and authorization, significant differences exist:
- Data Format: SAML uses XML for message passing, while OAuth uses JSON, making it more suitable for modern web applications.
- Focus: SAML is geared toward enterprise security and typically involves browser-based session cookies. OAuth utilizes API calls, providing a smoother experience for mobile applications, game consoles, and IoT devices.
- Use Cases: SAML excels in short-lived work environments, while OAuth is better suited for scenarios where frequent logins are undesirable, such as smart home devices.
Real-World OAuth Examples
The most straightforward example is the “Sign in with…” option you often see on websites. This allows you to use your existing login credentials from another service (like Google or Facebook) to access the new site. The first website (the consumer) only verifies that you are authenticated with the service provider.
Facebook apps provide another excellent use case. If an app requests permission to access your profile and pictures, Facebook (the service provider) manages the authorization using OAuth. You, as the user, grant the app (the consumer) specific access to your data.
Smart home devices also commonly employ OAuth, using confidential authorization. This allows them to sync with each other and be managed remotely without requiring constant re-authentication.
Authorization, Not Authentication: The Core Principle
It’s crucial to remember that OAuth is about authorization, not authentication. Authentication verifies your identity, while authorization grants permission to perform actions. OAuth doesn’t transmit authentication data but rather acts as an authorization token.
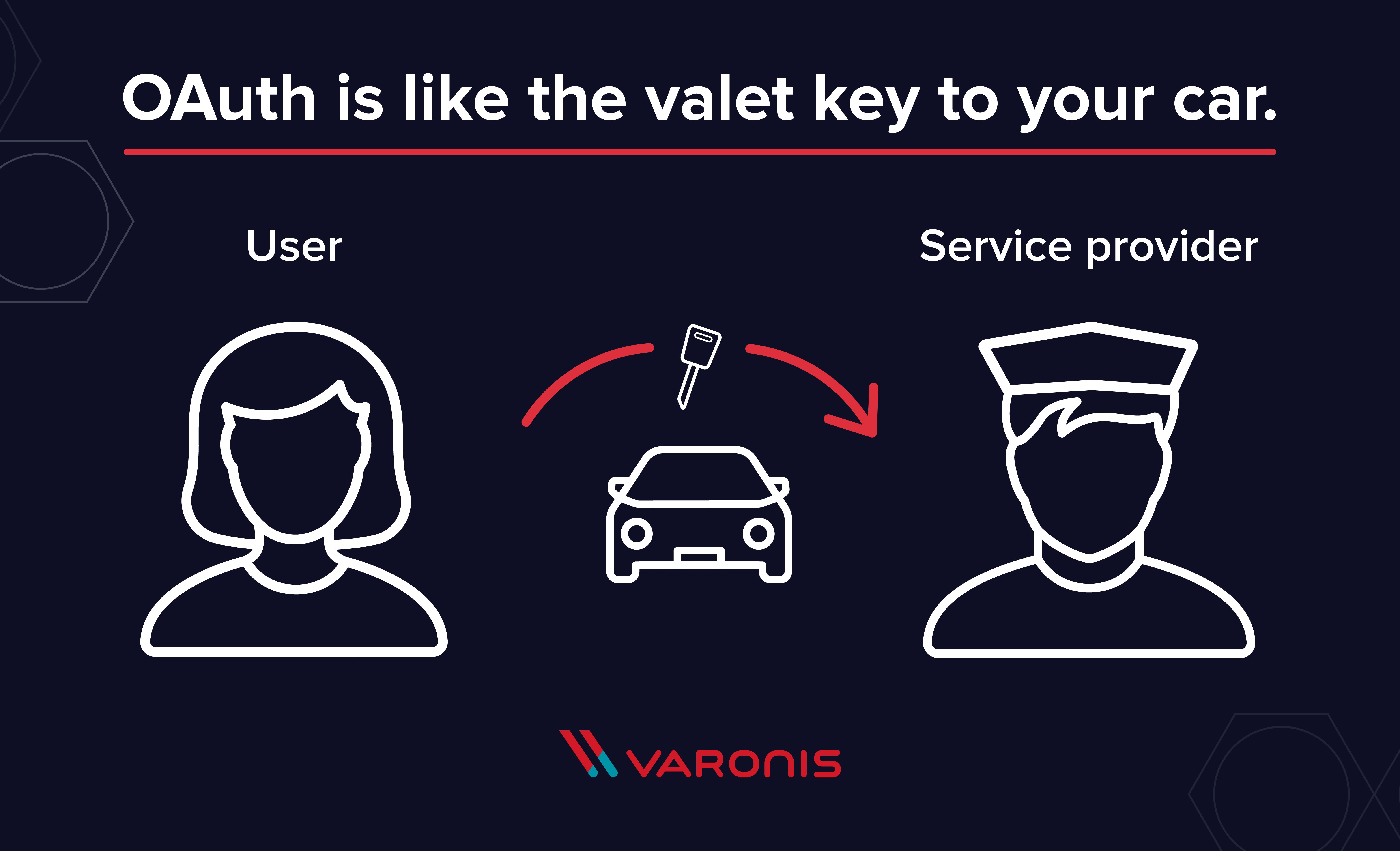
Think of it like a valet key to your car. It allows the valet to start and move the car but doesn’t provide access to the trunk or glove box. An OAuth token functions similarly, granting limited access to specific resources without revealing your full credentials. You control what each consumer can access from each service provider, essentially providing different “valet keys” for each.
How OAuth Works: The OAuth Love Triangle
An OAuth transaction involves three main players:
- User: The individual granting access.
- Consumer: The application requesting access.
- Service Provider: The platform controlling the user’s data.
Consider a scenario where Joe wants Bitly to post shortened links to his Twitter stream. Here’s a simplified breakdown of the process:
- User Shows Intent: Joe tells Bitly he wants them to post links to his Twitter.
- Consumer Gets Permission: Bitly requests a request token from Twitter. Twitter issues a token and a secret (to prevent forgery).
- User is Redirected to Service Provider: Bitly sends Joe to Twitter for approval, including the request token. Important: Always verify the URL to avoid phishing scams.
- User Gives Permission: Joe authorizes the request token with Twitter. Twitter confirms the authorization and marks the token as “good-to-go.”
- Consumer Obtains an Access Token: Bitly exchanges the request token for an access token and secret from Twitter.
- Consumer Accesses the Protected Resource: Bitly uses the access token to post the link to Joe’s Twitter stream.
In this process, Joe never shares his Twitter password with Bitly. He delegates access using OAuth in a secure manner. He can also revoke access at any time on Twitter, and OAuth allows for granular permission levels, giving different applications varying levels of access.
OAuth 1.0 vs. OAuth 2.0: A Significant Upgrade
OAuth 2.0 represents a complete redesign of OAuth 1.0, with the two versions being incompatible. For new applications, OAuth 2.0 is the recommended choice. OAuth 1.0 is now deprecated due to its complexity and scalability limitations.
OAuth 2.0 offers a faster and simpler implementation. It supports various flows for different application types and requirements, enabling signed secrets over HTTPS.
Conclusion: Embrace Secure Authorization
Understanding what is OAuth is essential in today’s interconnected digital world. It empowers you to grant applications access to your data on other platforms without compromising your credentials. By using authorization tokens instead of passwords, OAuth enhances security and provides greater control over your online privacy. So, the next time you see “Sign-in with…”, you’ll have a better understanding of the secure authorization process happening behind the scenes.