Phishing is a type of cybercrime where attackers impersonate legitimate institutions or individuals to deceive victims into revealing sensitive information. These attacks often occur through email, telephone, or text message, and aim to steal personally identifiable information (PII), banking details, credit card numbers, and passwords. The stolen data is then used to access accounts, commit identity theft, and cause financial harm.
The first recorded phishing lawsuit dates back to 2004, involving a teenager who created a fake “America Online” website to steal credit card information. Since then, phishing has evolved beyond email and websites to include “vishing” (voice phishing), “smishing” (SMS phishing), and numerous other techniques. Cybercriminals are constantly developing new and sophisticated methods to trick unsuspecting users.
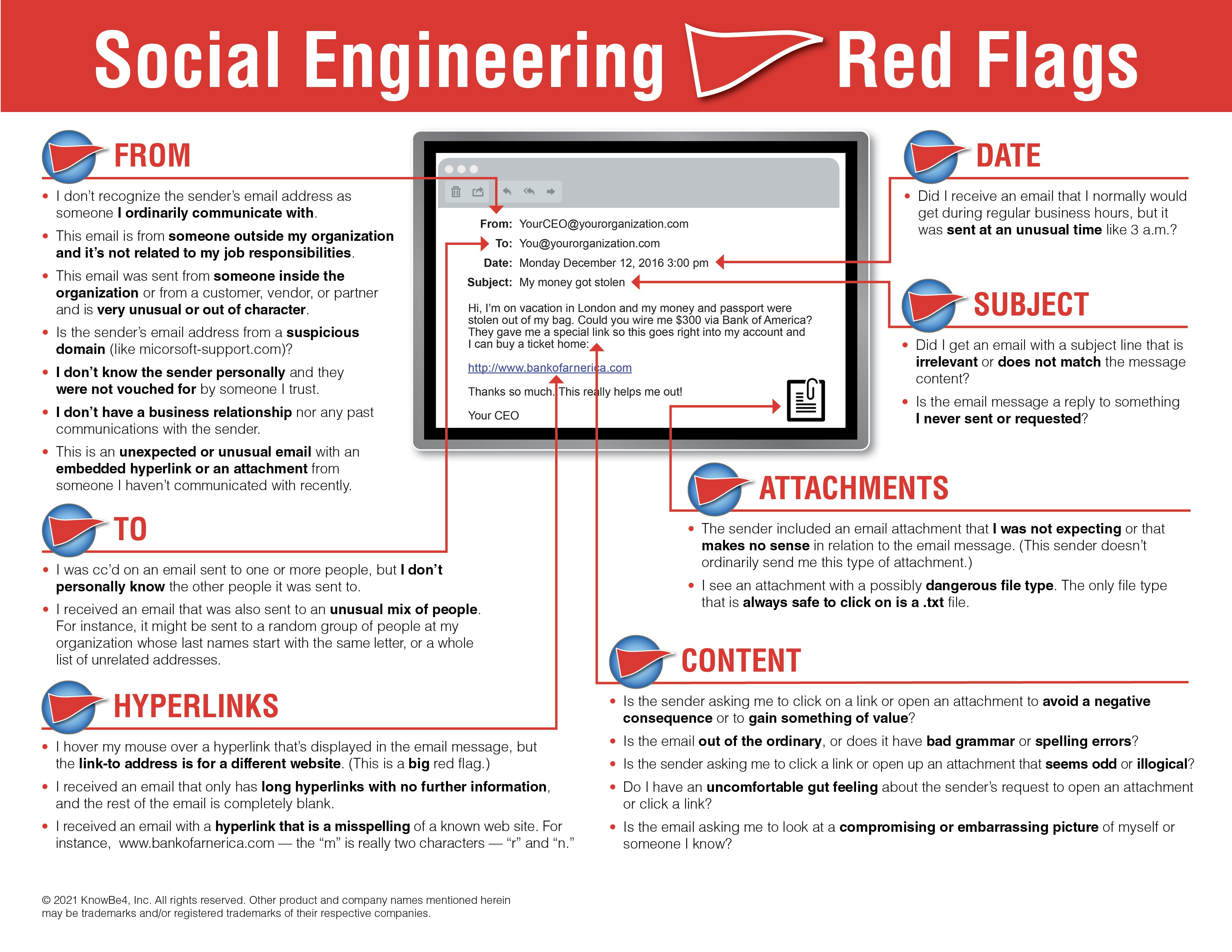
Key Characteristics of Phishing Emails
Recognizing the common traits of phishing emails is crucial for preventing attacks. Here are some tell-tale signs:
-
Offers That Seem Too Good to Be True: Phishing emails often promise lucrative rewards, such as winning an iPhone, a lottery, or another extravagant prize. These enticing offers are designed to grab your attention and bypass your skepticism. If an offer seems unrealistic, exercise extreme caution.
-
Sense of Urgency: Attackers frequently pressure recipients to act quickly, claiming that deals are time-sensitive or that immediate action is required. They might warn that your account will be suspended unless you update your details urgently. Legitimate organizations rarely demand immediate action or request sensitive information via email. When in doubt, contact the organization directly through official channels.
-
Suspicious Hyperlinks: A hyperlink’s displayed text can be misleading. Always hover over links to reveal the actual URL. Phishing emails often redirect to malicious websites that closely resemble legitimate ones but contain subtle misspellings (e.g., www.bankofarnerica.com instead of www.bankofamerica.com).
-
Unexpected Attachments: Avoid opening attachments from unknown or suspicious senders. These attachments often contain malware, such as ransomware or viruses. The only file type that is generally safe to open is a
.txtfile. -
Unusual Sender Information: Be wary of emails that appear out of character, unexpected, or generally suspicious, regardless of whether you recognize the sender. Attackers can spoof email addresses to impersonate trusted contacts.
 22 Social Engineering Red Flags
22 Social Engineering Red Flags
Preventing Phishing Attacks: Practical Strategies
While cybercriminals continually refine their tactics, several measures can be taken to safeguard against phishing attacks:
- Spam Filters: Implement spam filters to analyze incoming emails based on origin, sending software, and message content. While not foolproof, spam filters effectively block many phishing attempts.
- Browser Security Settings: Adjust browser settings to block access to known fraudulent websites. Browsers maintain lists of fake websites and will display alerts or prevent access to these sites.
- Password Management: Regularly change passwords and avoid using the same password across multiple accounts. Consider using a password manager to generate and store strong, unique passwords. Implementing a CAPTCHA system on websites can provide an additional layer of security.
- Financial Institution Monitoring: Banks and financial institutions employ monitoring systems to detect and prevent phishing attacks. Report suspected phishing attempts to industry groups so that legal action can be taken against fraudulent websites.
- Security Awareness Training: Organizations should provide security awareness training to employees to educate them about phishing risks and best practices for prevention.
- Careful Browsing Habits: Before entering sensitive information online, always verify the website’s legitimacy by contacting the company directly. When clicking a link in an email, hover over the URL to inspect it. Secure websites use HTTPS, indicated by a valid Secure Socket Layer (SSL) certificate.
- Verify Email Authenticity: Legitimate businesses, especially banks, generally avoid requesting personal information via email. If an email requests such information or threatens account suspension for non-compliance, it is likely a phishing attempt. Trusted institutions typically include account numbers or other personal details in their emails to verify their authenticity.
Free Phishing Security Test
Assess your vulnerability to phishing attacks with a free phishing security test. This test simulates real-world phishing scenarios to identify users who are prone to falling for these scams. It provides valuable insights into your organization’s security posture and helps you prioritize security awareness training efforts.
By understanding What Is Phish and implementing these preventive measures, individuals and organizations can significantly reduce their risk of falling victim to phishing attacks.
