Social engineering is a cunning and often underestimated threat in the realm of cybersecurity. It’s a broad term encompassing malicious activities that are executed through psychological manipulation, preying on human interaction rather than technical hacking. These attacks skillfully trick individuals into making security errors or divulging sensitive information, essentially exploiting human trust and vulnerabilities to gain unauthorized access or data.
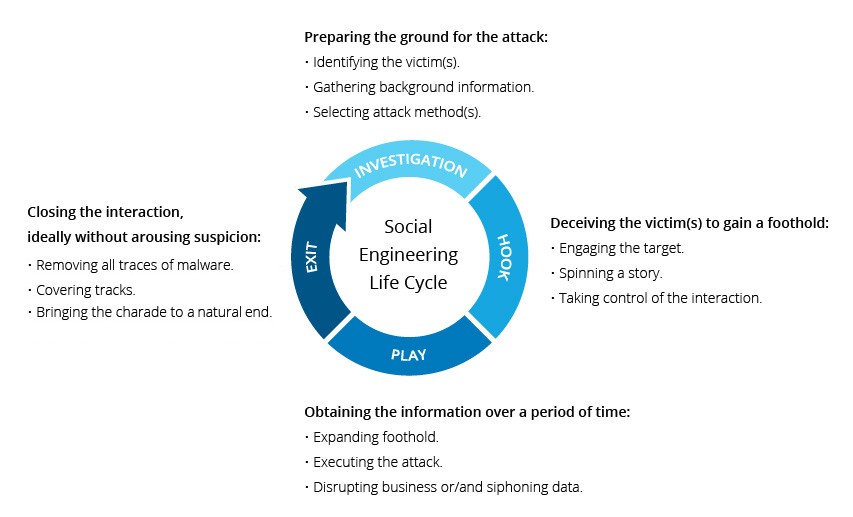
Social engineering attacks typically unfold in a multi-stage process. Initially, an attacker meticulously researches their target, gathering crucial background details. This reconnaissance phase aims to identify potential entry points and weaknesses in security protocols that can be exploited. Subsequently, the attacker focuses on building rapport and trust with the victim. This cultivated trust is then leveraged to stimulate specific actions that compromise security measures, such as revealing confidential data or granting access to protected systems and resources.
What distinguishes social engineering as a particularly potent threat is its reliance on human fallibility. It bypasses sophisticated technological defenses by targeting the weakest link in any security system: people. Mistakes made by well-meaning users are inherently unpredictable and far more challenging to detect and neutralize compared to traditional, malware-driven intrusions that target software or operating system vulnerabilities. This human-centric approach makes social engineering a persistent and evolving challenge for individuals and organizations alike.
Common Social Engineering Attack Techniques
Social engineering attacks manifest in diverse forms, exploiting various aspects of human behavior and communication. These attacks can occur in any context involving human interaction, both online and offline. Here are five prevalent types of digital social engineering assaults that individuals and businesses should be aware of:
Baiting: The Allure of False Promises
Baiting attacks operate on the principle of temptation, using false promises to trigger a victim’s curiosity or greed. These attacks lure unsuspecting users into traps designed to steal personal information or infect their systems with malware.
One notorious form of baiting involves the use of physical media to spread malware. Attackers strategically place infected devices, such as USB flash drives, in visible locations where targets are likely to find them. These “baits” often bear enticing labels, perhaps mimicking official documents like a company payroll list, to increase their appeal.
Unsuspecting victims, driven by curiosity, pick up these devices and insert them into their computers, either at work or home. This action triggers the automatic installation of malware, compromising the system.
Baiting schemes are not limited to the physical world. Online baiting tactics include using enticing advertisements that redirect users to malicious websites or encourage the download of malware-laden applications disguised as legitimate software.
Scareware: Exploiting Fear and Urgency
Scareware attacks rely on instilling fear and a sense of urgency in victims through fabricated alarms and nonexistent threats. Users are manipulated into believing their systems are infected with malware, prompting them to install software that offers no real benefit – except to the attacker – or is, in fact, malware itself. Scareware is also known by other names, including deception software, rogue security software, and fraudware.
A typical scareware tactic involves browser pop-up banners that mimic legitimate security alerts. These pop-ups often display alarming messages like, “Your computer may be infected with harmful spyware programs!” They then aggressively offer to install a “solution,” which is often either malware itself or a useless program, or direct the user to a malicious website designed to infect their computer.
Scareware is also distributed through spam emails containing fake warnings or enticing offers for worthless or harmful “security” services, further exploiting user anxieties about online threats.
Pretexting: Building Lies for Information Extraction
Pretexting attacks involve crafting elaborate scenarios and fabricated identities to deceive victims into divulging sensitive information. The attacker, known as a “pretexter,” typically initiates contact by pretending to need specific information from the victim to perform a supposedly critical task.
A key element of pretexting is establishing trust. Attackers commonly impersonate authority figures or individuals the victim is likely to trust, such as colleagues, law enforcement officers, bank representatives, or tax officials. The pretexter then asks seemingly innocuous questions, claiming they are necessary to verify the victim’s identity. However, these questions are carefully designed to extract valuable personal data.
Through this deceptive approach, pretexters can gather a wide range of sensitive information, including social security numbers, home addresses, phone numbers, call logs, vacation schedules, bank account details, and even physical security information related to facilities.
Phishing: Casting a Wide Net for Credentials
Phishing is one of the most widespread and recognizable types of social engineering attacks. Phishing scams are typically conducted through email and text message campaigns designed to create a sense of urgency, curiosity, or fear in recipients. The ultimate goal is to manipulate victims into revealing sensitive information, clicking on malicious links that lead to fake websites, or opening attachments containing malware.
A classic phishing example is an email that appears to be from a legitimate online service provider. The email might alert users to a purported policy violation or security issue requiring immediate action, such as a mandatory password change. Crucially, the email includes a link that deceptively directs the user to a fraudulent website. This fake website is meticulously designed to closely resemble the legitimate site, tricking the unsuspecting user into entering their current login credentials and a new password. Once submitted, this information is instantly sent to the attacker, granting them unauthorized access to the victim’s account.
Due to the mass-mailing nature of many phishing campaigns, where identical or near-identical messages are sent to numerous users, email servers equipped with threat intelligence and sharing platforms are often able to detect and block these attacks with relative ease.
Spear Phishing: Highly Targeted and Personalized Attacks
Spear phishing is a more sophisticated and targeted variation of the standard phishing scam. Instead of broad, indiscriminate campaigns, spear phishing attackers carefully select specific individuals or organizations as their targets. They then meticulously tailor their deceptive messages based on in-depth research into the victim’s characteristics, job roles, professional contacts, and other personal details. This personalization makes spear phishing attacks far less conspicuous and significantly more effective.
Spear phishing demands considerably more effort and reconnaissance from the attacker and can often take weeks or even months to execute successfully. However, the highly targeted nature of these attacks makes them significantly harder to detect by automated systems and, consequently, they often achieve higher success rates compared to generic phishing attempts.
For instance, a spear phishing scenario might involve an attacker impersonating an IT consultant known to an organization. The attacker sends a carefully crafted email to specific employees, using language, tone, and even a signature that convincingly mimics the consultant’s usual communications. The deceptive email might urge recipients to immediately change their passwords and conveniently provides a link. However, this link redirects to a malicious webpage controlled by the attacker, designed to capture the employee’s credentials when they attempt to log in.
Social Engineering Prevention: Building Human Firewalls
Social engineers excel at exploiting human emotions, such as curiosity, fear, and trust, to manipulate victims and ensnare them in their schemes. Therefore, cultivating a sense of vigilance and healthy skepticism is crucial in defending against these attacks. Be particularly cautious when you feel a strong emotional response to an email, are overly enticed by an online offer, or encounter unfamiliar digital media left in public places. Maintaining a state of alertness can significantly enhance your protection against the majority of social engineering attacks prevalent in the digital landscape.
In addition to general vigilance, implementing these preventative measures can further strengthen your defenses against social engineering tactics:
-
Exercise Caution with Emails and Attachments from Unknown Senders: If you don’t recognize the sender of an email, or if something about the message feels suspicious, it’s best to err on the side of caution and avoid opening it. Even if you recognize the sender, but the email’s content seems unusual or out of character, verify the message’s legitimacy through alternative channels. Contact the sender via phone or directly through the service provider’s official website to confirm. Remember that email addresses can be easily spoofed, meaning an email appearing to originate from a trusted source could, in reality, be from an attacker.
-
Implement Multi-Factor Authentication (MFA): User credentials, such as usernames and passwords, are prime targets for social engineers. Enabling multi-factor authentication adds a crucial layer of security to your accounts. MFA requires users to provide an additional verification factor beyond just a password, such as a code from a mobile app or a fingerprint scan. This significantly strengthens account protection, even if your password is compromised through a social engineering attack.
-
Be Skeptical of Tempting Offers and “Too Good To Be True” Scenarios: If an offer appears exceptionally attractive or too good to be true, it likely is. Approach such offers with healthy skepticism and resist the urge to act impulsively. Conduct independent research by using search engines to investigate the offer’s legitimacy. Often, a quick online search can reveal whether you are dealing with a genuine opportunity or a deceptive trap.
-
Maintain Up-to-Date Antivirus and Antimalware Software: Robust antivirus and antimalware software are essential components of any cybersecurity strategy. Ensure that your security software is always updated with the latest virus definitions and security patches. Enable automatic updates to ensure continuous protection, or make it a routine to manually download the latest updates daily. Regularly scan your systems for potential infections to proactively detect and remove any malware that may have bypassed initial defenses.