What Is Sso? Single Sign-On is a user authentication method, a streamlined approach allowing users to access multiple applications with just one set of login credentials, simplifying digital identity management. WHAT.EDU.VN offers an easy way to understand complex topics. Learn about password management, access control, and identity verification.
1. Understanding Single Sign-On (SSO)
Single Sign-On (SSO) is a user authentication process that allows users to access multiple applications and websites with a single set of credentials. Instead of needing a different username and password for each application, users can use one identity to access all of them. This streamlines the login process and enhances user experience. Think of it as having one master key that unlocks all the doors in your digital world, offering convenience and simplified identity solutions.
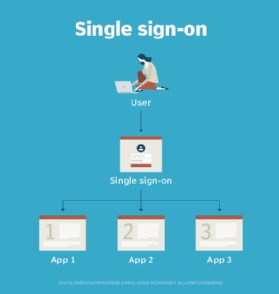 Diagram illustrating how single sign-on (SSO) simplifies access to multiple applications for a user.
Diagram illustrating how single sign-on (SSO) simplifies access to multiple applications for a user.
1.1. Core Components of SSO
SSO systems typically involve three primary components:
- The User: The individual attempting to access multiple applications.
- The Identity Provider (IdP): The system that manages and authenticates user identities.
- The Service Provider (SP): The applications or websites the user is trying to access.
1.2. Benefits of Using SSO
Using SSO offers numerous advantages for both users and organizations, including improved productivity and enhanced security.
- Improved User Experience: Simplifies the login process, reducing the need to remember multiple usernames and passwords.
- Enhanced Security: Centralizes authentication, making it easier to enforce security policies and monitor access.
- Increased Productivity: Reduces time spent on login-related tasks, allowing users to focus on their primary responsibilities.
- Reduced IT Costs: Decreases the number of help desk requests related to password resets and login issues.
2. How Does SSO Work?
The SSO process begins when a user attempts to access an application. The application redirects the user to the Identity Provider (IdP) for authentication. Once the user is authenticated by the IdP, they are granted access to the application, and the process is completed seamlessly.
2.1. Detailed SSO Workflow
- User Access Attempt: A user tries to access an application or website (the Service Provider).
- Redirection to IdP: The Service Provider redirects the user to the Identity Provider (e.g., Okta, Azure AD).
- Authentication: The user provides their credentials to the Identity Provider.
- Token Issuance: The Identity Provider verifies the credentials and issues a security token.
- Token Validation: The Service Provider validates the security token.
- Access Granted: The user is granted access to the application without needing to enter additional credentials.
2.2. Protocols Used in SSO
Several protocols are used to implement SSO, each with its own strengths and weaknesses. Some of the most common protocols include SAML, OAuth, and OpenID Connect.
- Security Assertion Markup Language (SAML): SAML is an XML-based open standard for exchanging authentication and authorization data between parties, particularly between an Identity Provider and a Service Provider. SAML enables web-based, cross-domain single sign-on, reducing the burden of distributing multiple credentials to the user.
- OAuth: OAuth is an open standard for access delegation, commonly used to grant websites or applications access to their information on other websites but without giving them the passwords. OAuth relies on security tokens that grant access to a specific set of resources and for a defined period.
- OpenID Connect (OIDC): OpenID Connect is an authentication layer on top of OAuth 2.0. It allows clients to verify the identity of the end-user based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner. OpenID Connect allows developers to authenticate their users across websites and apps without having to own and manage password files.
3. Types of SSO Implementations
There are various types of SSO implementations, each designed to meet specific organizational needs and security requirements. Understanding these different types can help organizations choose the best SSO solution for their environment.
3.1. Cloud-Based SSO
Cloud-based SSO solutions are hosted in the cloud and offer a centralized authentication service for accessing cloud-based applications. These solutions are typically offered as a service (SaaS) and provide easy integration with various cloud applications.
- Benefits: Scalability, ease of deployment, and reduced infrastructure costs.
- Examples: Okta, OneLogin, and Azure Active Directory.
3.2. On-Premise SSO
On-premise SSO solutions are hosted within the organization’s own infrastructure. These solutions provide greater control over the authentication process and are often preferred by organizations with strict security and compliance requirements.
- Benefits: Greater control, enhanced security, and compliance with regulatory requirements.
- Examples: Ping Identity, IBM Security Access Manager, and Oracle Access Manager.
3.3. Hybrid SSO
Hybrid SSO solutions combine elements of both cloud-based and on-premise SSO. These solutions allow organizations to leverage the benefits of both cloud and on-premise environments, providing flexibility and scalability.
- Benefits: Flexibility, scalability, and a balance between control and ease of use.
- Examples: A combination of Azure AD Connect with on-premise Active Directory Federation Services (ADFS).
4. SSO Security Considerations
While SSO offers numerous benefits, it also introduces certain security risks. Organizations must implement robust security measures to protect their SSO infrastructure and mitigate potential threats.
4.1. Common SSO Security Risks
- Single Point of Failure: If the SSO system is compromised, attackers can gain access to all applications that rely on it.
- Phishing Attacks: Attackers may attempt to steal user credentials through phishing attacks, gaining access to the SSO system.
- Session Hijacking: Attackers may attempt to hijack user sessions, gaining unauthorized access to applications.
4.2. Best Practices for SSO Security
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring users to provide multiple forms of authentication.
- Strong Password Policies: Enforcing strong password policies helps prevent attackers from guessing or cracking user passwords.
- Regular Security Audits: Conducting regular security audits helps identify and address potential vulnerabilities in the SSO infrastructure.
- Session Management: Implementing robust session management practices helps prevent session hijacking and unauthorized access.
5. Implementing SSO in Your Organization
Implementing SSO requires careful planning and execution. Organizations should follow a structured approach to ensure a successful implementation.
5.1. Steps to Implement SSO
- Assess Requirements: Identify the applications and users that will be included in the SSO implementation.
- Choose an SSO Solution: Select an SSO solution that meets the organization’s needs and security requirements.
- Configure the IdP: Configure the Identity Provider with user identities and authentication policies.
- Integrate Applications: Integrate the applications with the SSO solution, configuring them to rely on the IdP for authentication.
- Test the Implementation: Thoroughly test the SSO implementation to ensure it is working correctly.
- Deploy the Solution: Deploy the SSO solution to the production environment.
- Monitor and Maintain: Continuously monitor and maintain the SSO solution to ensure it remains secure and effective.
5.2. Key Considerations for Successful Implementation
- User Training: Provide users with training on how to use the SSO system.
- Communication: Communicate the benefits of SSO to users and stakeholders.
- Support: Provide ongoing support to users and address any issues that arise.
- Scalability: Ensure the SSO solution is scalable to meet the organization’s future needs.
6. SSO and Compliance
Compliance is a critical consideration for organizations implementing SSO, especially those in regulated industries. Understanding the relevant compliance standards and ensuring that the SSO implementation aligns with these standards is essential for maintaining regulatory compliance and avoiding penalties.
6.1. Relevant Compliance Standards
Several compliance standards are relevant to SSO implementations, depending on the industry and geographic location of the organization. Some of the most common compliance standards include:
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA sets the standard for sensitive patient data protection. Organizations in the healthcare industry must ensure that their SSO implementation complies with HIPAA requirements for access control and data security.
- PCI DSS (Payment Card Industry Data Security Standard): PCI DSS is a set of security standards designed to protect credit card information. Organizations that process credit card payments must ensure that their SSO implementation complies with PCI DSS requirements for access control and data encryption.
- GDPR (General Data Protection Regulation): GDPR is a European Union regulation that sets the standard for data protection and privacy. Organizations that process the personal data of EU citizens must ensure that their SSO implementation complies with GDPR requirements for data security and privacy.
- SOC 2 (Service Organization Control 2): SOC 2 is a set of auditing standards developed by the American Institute of Certified Public Accountants (AICPA). SOC 2 reports assess the security, availability, processing integrity, confidentiality, and privacy of service providers’ systems. Organizations that use service providers for SSO must ensure that these providers have SOC 2 compliance.
6.2. Ensuring Compliance with SSO
To ensure compliance with relevant standards, organizations should take the following steps when implementing SSO:
- Conduct a Compliance Assessment: Perform a thorough assessment of the compliance requirements that apply to the organization.
- Select a Compliant SSO Solution: Choose an SSO solution that is designed to meet the organization’s compliance requirements.
- Configure SSO for Compliance: Configure the SSO solution to enforce the organization’s compliance policies.
- Monitor Compliance: Continuously monitor the SSO implementation to ensure ongoing compliance.
- Regular Audits: Conduct regular audits to verify that the SSO solution is operating in compliance with relevant standards.
By addressing compliance considerations during the SSO implementation process, organizations can reduce the risk of non-compliance and ensure that their SSO solution supports their overall compliance objectives.
7. The Future of SSO
The future of SSO is evolving rapidly, driven by advancements in technology and changing user expectations. Several trends are shaping the future of SSO, including passwordless authentication, decentralized identity, and AI-driven security.
7.1. Emerging Trends in SSO
- Passwordless Authentication: Passwordless authentication methods, such as biometric authentication and security keys, are becoming increasingly popular as a more secure and user-friendly alternative to traditional passwords.
- Decentralized Identity: Decentralized identity solutions, based on blockchain technology, are emerging as a way to give users greater control over their digital identities.
- AI-Driven Security: Artificial intelligence (AI) is being used to enhance SSO security by detecting and preventing fraudulent access attempts.
7.2. Predictions for SSO Technology
- Increased Adoption of Passwordless Authentication: Passwordless authentication will become the norm, replacing traditional passwords for many applications.
- Greater Integration with Biometric Technologies: Biometric technologies, such as fingerprint scanning and facial recognition, will be integrated into SSO solutions for enhanced security and user experience.
- Enhanced Security Through AI and Machine Learning: AI and machine learning will be used to detect and prevent sophisticated cyber attacks, making SSO systems more secure than ever before.
8. SSO vs. Multi-Factor Authentication (MFA)
SSO and Multi-Factor Authentication (MFA) are both important security measures, but they serve different purposes. Understanding the differences between SSO and MFA is essential for implementing a comprehensive security strategy.
8.1. Key Differences Between SSO and MFA
- SSO: Simplifies the login process by allowing users to access multiple applications with a single set of credentials.
- MFA: Adds an extra layer of security by requiring users to provide multiple forms of authentication.
8.2. Combining SSO and MFA for Enhanced Security
Combining SSO and MFA provides a robust security solution that offers both convenience and security. By implementing MFA on top of SSO, organizations can ensure that even if a user’s SSO credentials are compromised, attackers will still need to provide additional forms of authentication to gain access to applications.
8.3. Advantages of Using SSO with MFA
- Enhanced Security: MFA adds an extra layer of security to the SSO implementation.
- Improved User Experience: SSO simplifies the login process, while MFA ensures that access is secure.
- Compliance: Using SSO with MFA helps organizations meet compliance requirements for access control and data security.
9. Common Mistakes to Avoid When Implementing SSO
Implementing Single Sign-On (SSO) can significantly enhance security and user experience, but it’s crucial to avoid common pitfalls. Here are some frequent mistakes to steer clear of:
9.1. Neglecting Security Considerations
Insufficient Authentication Measures
Failing to implement Multi-Factor Authentication (MFA) as an additional layer of security.
- Solution: Always integrate MFA to protect against compromised credentials.
Weak Encryption Protocols
Using outdated or weak encryption methods for data transmission and storage.
- Solution: Adopt strong, up-to-date encryption standards such as AES-256.
Inadequate Session Management
Poorly managing user sessions, leading to vulnerabilities like session hijacking.
- Solution: Implement secure session management practices, including session timeouts and regular re-authentication.
9.2. Poor Planning and Integration
Lack of a Comprehensive Strategy
Implementing SSO without a clear understanding of organizational needs and goals.
- Solution: Develop a detailed SSO strategy aligning with business objectives and security requirements.
Ignoring Application Compatibility
Failing to assess the compatibility of all applications with the SSO system.
- Solution: Conduct thorough compatibility testing and plan for necessary modifications.
Inadequate Testing
Deploying SSO without sufficient testing across different scenarios and user groups.
- Solution: Perform comprehensive testing, including user acceptance testing (UAT), before full deployment.
9.3. Overlooking User Experience
Complicated Login Processes
Creating overly complex or confusing login procedures for users.
- Solution: Design intuitive and user-friendly login experiences.
Lack of User Training
Failing to provide adequate training and support for users transitioning to SSO.
- Solution: Offer comprehensive training programs and ongoing support to ensure smooth adoption.
Ignoring Feedback
Ignoring user feedback and failing to address usability issues.
- Solution: Actively solicit and respond to user feedback to continuously improve the SSO system.
9.4. Neglecting Maintenance and Updates
Ignoring System Updates
Failing to regularly update the SSO system with the latest security patches and improvements.
- Solution: Establish a routine for applying updates and patches promptly.
Inadequate Monitoring
Not monitoring the SSO system for performance issues, security breaches, or unauthorized access attempts.
- Solution: Implement continuous monitoring and alerting systems to detect and respond to potential issues.
Poor Documentation
Lacking comprehensive documentation for the SSO system, making troubleshooting and maintenance difficult.
- Solution: Maintain detailed documentation, including configuration settings, troubleshooting steps, and emergency procedures.
10. FAQs About SSO
Here are some frequently asked questions (FAQs) about Single Sign-On (SSO), designed to provide quick and clear answers to common queries.
| Question | Answer |
|---|---|
| What is Single Sign-On (SSO)? | SSO is an authentication method that allows users to access multiple applications with a single set of login credentials. |
| How does SSO improve user experience? | SSO eliminates the need for users to remember multiple usernames and passwords, streamlining the login process and reducing the time spent on authentication. |
| What are the main protocols used in SSO? | The main protocols used in SSO include SAML (Security Assertion Markup Language), OAuth, and OpenID Connect (OIDC). |
| What is an Identity Provider (IdP)? | An Identity Provider is a system that manages and authenticates user identities. It verifies user credentials and issues security tokens that allow users to access applications. |
| What is a Service Provider (SP)? | A Service Provider is an application or website that relies on an Identity Provider to authenticate users. When a user tries to access the SP, they are redirected to the IdP for authentication. |
| What are the security benefits of using SSO? | SSO centralizes authentication, making it easier to enforce security policies, monitor access, and implement multi-factor authentication (MFA). |
| What are the risks associated with SSO? | The main risk associated with SSO is that it creates a single point of failure. If the SSO system is compromised, attackers can gain access to all applications that rely on it. |
| How can SSO security risks be mitigated? | SSO security risks can be mitigated by implementing multi-factor authentication (MFA), using strong password policies, conducting regular security audits, and implementing robust session management practices. |
| What is the difference between SSO and MFA? | SSO simplifies the login process, while MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. |
| Can SSO be used with cloud-based applications? | Yes, SSO can be used with cloud-based applications. Cloud-based SSO solutions provide a centralized authentication service for accessing cloud applications. |
| What is passwordless authentication? | Passwordless authentication refers to methods of authentication that do not require users to enter a traditional password. Examples include biometric authentication (fingerprint, facial recognition) and security keys. |
| How does decentralized identity relate to SSO? | Decentralized identity solutions, often based on blockchain technology, give users greater control over their digital identities. This can enhance SSO by allowing users to manage their identities across multiple platforms without relying on a central authority. |
| What role does AI play in the future of SSO? | AI is used to enhance SSO security by detecting and preventing fraudulent access attempts. AI algorithms can analyze login patterns and user behavior to identify and block suspicious activity. |
| What compliance standards are relevant to SSO? | Relevant compliance standards include HIPAA (for healthcare), PCI DSS (for payment card industry), GDPR (for data protection in the EU), and SOC 2 (for service organizations). |
| How do I ensure my SSO implementation is compliant? | To ensure compliance, conduct a compliance assessment, select a compliant SSO solution, configure SSO for compliance, monitor compliance continuously, and conduct regular audits. |
| What are some common mistakes to avoid when implementing SSO? | Common mistakes include neglecting security considerations, poor planning and integration, overlooking user experience, and neglecting maintenance and updates. |
| How can I ensure a smooth transition to SSO for my users? | Provide comprehensive training, communicate the benefits of SSO, offer ongoing support, and actively solicit user feedback. |
Still have questions? Visit WHAT.EDU.VN to ask your questions and get answers for free. Our community of experts is ready to help you understand SSO and other complex topics.
Simplify Your Life with Easy Answers at WHAT.EDU.VN
Finding quick, reliable answers to your questions shouldn’t be a struggle. At WHAT.EDU.VN, we understand the challenges of navigating the sea of information. That’s why we’ve created a platform where asking questions is not only easy but also completely free. Whether you’re a student tackling tough homework, a professional seeking expert insights, or simply a curious mind eager to learn, WHAT.EDU.VN is your go-to resource.
Why Choose WHAT.EDU.VN?
- Free Access: Ask any question without worrying about subscription fees or hidden costs.
- Fast Responses: Get timely answers from knowledgeable experts and community members.
- Comprehensive Information: Dive deep into topics with clear, easy-to-understand explanations.
- Community Support: Connect with others who share your interests and learn from diverse perspectives.
Ready to Get Started?
Don’t let unanswered questions hold you back. Join the WHAT.EDU.VN community today and experience the ease of finding the information you need, right when you need it.
Ask Your Question Now!
Contact Us
Address: 888 Question City Plaza, Seattle, WA 98101, United States
WhatsApp: +1 (206) 555-7890
Website: WHAT.EDU.VN
We’re here to help you explore, understand, and succeed. Welcome to what.edu.vn – where curiosity meets clarity.