Contact Key Verification explained. Want to ensure your iMessage conversations are secure? WHAT.EDU.VN is here to provide a comprehensive breakdown of Contact Key Verification, its benefits, and how to use it effectively. Explore enhanced security measures, digital identity verification, and secure communication strategies with our guide. Learn about authentication methods and encryption techniques, empowering you to safeguard your communications.
1. Understanding Contact Key Verification: The Basics
What Is Contact Key Verification, and why is it becoming increasingly important in today’s digital landscape? Contact key verification is a security feature designed to ensure that you are communicating with the intended person and nobody else. It acts as a digital handshake, confirming the authenticity of the parties involved in a conversation. In essence, it’s about establishing trust in a world where digital identities can be easily spoofed.
1.1. Defining Contact Key Verification
Contact key verification is a process that validates the identity of a contact by comparing cryptographic keys. This process helps to prevent man-in-the-middle attacks, where an attacker intercepts and alters communications between two parties. By verifying the contact’s key, you can be confident that your messages are going to the right person.
Think of it like this: Imagine you’re sending a letter through the mail. Normally, you just write the address on the envelope and hope it gets to the right person. But with contact key verification, it’s like adding a special seal to the envelope that only the intended recipient can open. This seal ensures that the letter hasn’t been tampered with and that it’s reaching the correct person.
1.2. The Core Concepts Behind Contact Key Verification
Several core concepts underpin how contact key verification functions:
- Cryptography: The use of encryption and decryption to secure communication.
- Public Key Infrastructure (PKI): A system for creating, managing, and validating digital certificates.
- Hashing: Converting data into a unique, fixed-size string of characters (a hash) to verify its integrity.
- Digital Signatures: Using a private key to sign data, allowing others to verify the authenticity and integrity of the data using the corresponding public key.
These concepts work together to create a robust system for verifying the identity of contacts in digital communications. Cryptography ensures that messages are encrypted and cannot be read by unauthorized parties. PKI provides a framework for managing digital certificates, which are used to verify the identity of contacts. Hashing ensures that data is not tampered with during transmission. Digital signatures provide a way to verify the authenticity and integrity of data.
1.3. How Contact Key Verification Works
The process typically involves the following steps:
- Key Exchange: The sender and receiver exchange public keys.
- Verification Code Generation: The system generates a unique verification code based on the exchanged keys.
- Manual Comparison: The sender and receiver compare the verification codes through a secure channel (e.g., in person, via a trusted phone call).
- Verification Completion: If the codes match, the contact is marked as verified, ensuring future communications are secure.
Let’s break down this process with an example. Suppose Alice wants to verify Bob’s contact key. First, Alice and Bob exchange their public keys. Then, their messaging app generates a unique verification code based on these keys. Alice and Bob then meet in person or talk over a secure phone line to compare these codes. If the codes match, Alice can be confident that she is communicating with the real Bob, and she marks his contact as verified in her app. From then on, all communications between Alice and Bob are secured and verified.
1.4. The Importance of Digital Trust
In an age where digital impersonation and phishing attacks are rampant, establishing digital trust is more critical than ever. Contact key verification provides a mechanism to create a secure and trusted communication environment, reducing the risk of falling victim to malicious actors.
Consider the implications of not verifying your contacts. You could be communicating with an imposter who is trying to steal your personal information, spread misinformation, or commit fraud. By verifying your contacts, you are taking a proactive step to protect yourself and your data.
1.5. Contact Key Verification vs. End-to-End Encryption
While both are crucial for secure communication, they serve different purposes. End-to-end encryption ensures that only the sender and receiver can read the messages, while contact key verification ensures you’re actually communicating with the intended recipient. They work best when used together.
End-to-end encryption protects the content of your messages, while contact key verification protects the identity of the person you are communicating with. Imagine sending a valuable package. End-to-end encryption is like putting the package in a locked box, so no one can see what’s inside. Contact key verification is like verifying the recipient’s ID before handing over the package, ensuring it goes to the right person.
2. Benefits of Using Contact Key Verification
Why should you use contact key verification? The benefits extend beyond simple security, offering a more secure and reliable communication experience. Here are the primary advantages:
2.1. Enhanced Security Against Impersonation
Contact key verification significantly reduces the risk of communicating with imposters. By verifying the contact’s key, you can be confident that you’re talking to the right person.
Think about a scenario where a malicious actor tries to impersonate your bank. They might send you an email or text message asking for your login credentials. If you haven’t verified the contact key, you might fall for the scam and provide your information to the imposter. However, with contact key verification, you can verify that the communication is indeed coming from your bank, preventing you from becoming a victim of fraud.
2.2. Protection Against Man-in-the-Middle Attacks
This feature helps to prevent man-in-the-middle attacks, where an attacker intercepts and alters communications between two parties.
Imagine you’re sending a confidential document to your lawyer. Without contact key verification, a hacker could intercept the message, change the contents, and then send it on to your lawyer, making it appear as if it came from you. This could have serious consequences, especially if the document contains sensitive legal or financial information. However, with contact key verification, your lawyer can verify that the message is indeed coming from you and that it hasn’t been tampered with, providing a much higher level of security.
2.3. Increased Confidence in Digital Communications
Knowing that your contacts are verified provides peace of mind, making digital interactions more trustworthy and secure.
In today’s digital world, trust is a valuable commodity. With so many scams and phishing attacks, it’s easy to become suspicious of online communications. Contact key verification helps to restore trust by providing a way to verify the identity of your contacts. This can lead to more open and honest communication, both personally and professionally.
2.4. Maintaining Data Integrity
By ensuring that your communications are not tampered with, contact key verification helps maintain the integrity of your data.
Data integrity is crucial in many areas, such as finance, healthcare, and law. If data is compromised, it can lead to serious errors, fraud, or legal problems. Contact key verification helps to ensure that your data remains accurate and reliable by preventing unauthorized access and tampering.
2.5. Compliance with Security Standards
For businesses and organizations, using contact key verification can help meet compliance requirements with various security standards and regulations.
Many industries are subject to strict security standards and regulations, such as HIPAA in healthcare or GDPR in Europe. Contact key verification can help organizations meet these requirements by providing a way to secure their communications and protect sensitive data. This can help to avoid costly fines and legal liabilities.
3. How to Implement Contact Key Verification
Implementing contact key verification might seem daunting, but many platforms are making it increasingly accessible. Here’s a step-by-step guide to get you started:
3.1. Checking Platform Compatibility
First, ensure that the messaging or communication platform you use supports contact key verification. Popular apps like Signal, WhatsApp (for certain features), and iMessage (with the Contact Key Verification feature) offer this capability.
Before you can implement contact key verification, you need to make sure that your messaging platform supports it. Some platforms, like Signal, have contact key verification built in and enabled by default. Others, like WhatsApp, offer contact key verification as an optional feature. And some platforms don’t support contact key verification at all.
3.2. Enabling Contact Key Verification
Navigate to the security settings of your messaging app and look for options like “Contact Key Verification” or “Verify Contact.” Enable this feature to start the verification process.
The process for enabling contact key verification varies depending on the platform you are using. In Signal, you can find the contact key verification option in the settings menu for each individual contact. In WhatsApp, you can find it under the “Security” settings. And in iMessage, you need to enable the “Contact Key Verification” feature in your Apple ID settings.
3.3. Verifying Contacts Manually
Most platforms offer a manual verification process. This usually involves comparing a unique code or key with your contact through a secure channel, such as a phone call or in person.
The manual verification process typically involves comparing a unique code or key with your contact. This code is generated by the messaging app and is unique to each contact. You and your contact need to compare the codes through a secure channel, such as a phone call or in person, to ensure that they match. If the codes match, you can be confident that you are communicating with the right person.
3.4. Using Public Verification Codes
Some platforms allow you to share your public verification code on social media or other public channels, making it easier for others to verify you.
Public verification codes are a convenient way to allow others to verify your identity without having to meet in person or talk on the phone. You can share your public verification code on social media, your website, or other public channels. Anyone who wants to verify your identity can then compare the code you have posted with the code displayed in their messaging app.
3.5. Regularly Checking Verification Status
Periodically check the verification status of your contacts to ensure that their keys haven’t changed, which could indicate a potential security issue.
Contact keys can change for various reasons, such as when a contact gets a new phone or re-installs their messaging app. It’s important to regularly check the verification status of your contacts to make sure that their keys haven’t changed. If a key has changed, you should re-verify the contact to ensure that you are still communicating with the right person.
4. Platforms Offering Contact Key Verification
Several messaging platforms have integrated contact key verification to enhance security. Here are some notable examples:
4.1. Signal
Signal is renowned for its strong emphasis on privacy and security, with contact key verification enabled by default.
Signal is widely regarded as one of the most secure messaging apps available. It uses end-to-end encryption to protect all communications, and it has contact key verification enabled by default. This means that you can be confident that your messages are private and that you are communicating with the right person.
4.2. WhatsApp
WhatsApp offers contact key verification as an optional feature, allowing users to manually verify contacts for added security.
WhatsApp is one of the most popular messaging apps in the world. While it offers end-to-end encryption, contact key verification is not enabled by default. However, users can manually verify their contacts by comparing a unique code. This provides an extra layer of security for those who need it.
4.3. iMessage (with Contact Key Verification)
Apple’s iMessage includes a Contact Key Verification feature that allows users to manually verify contacts for enhanced security.
iMessage is the default messaging app on Apple devices. It offers end-to-end encryption for messages sent between Apple users. The Contact Key Verification feature allows users to manually verify their contacts for added security. This is a valuable feature for those who want to ensure that their communications are as secure as possible.
4.4. Other Platforms
Other platforms like Telegram (Secret Chats) and Threema also provide contact key verification options.
While Signal, WhatsApp, and iMessage are the most well-known platforms offering contact key verification, there are other options available as well. Telegram’s Secret Chats feature provides end-to-end encryption and contact key verification. Threema is another messaging app that focuses on privacy and security, offering both end-to-end encryption and contact key verification.
4.5. Comparing Features
Each platform has its unique implementation of contact key verification. Some offer automatic verification, while others rely on manual processes. Evaluate your needs and choose a platform that aligns with your security requirements.
When choosing a messaging platform, it’s important to consider the features that are most important to you. If security is a top priority, you’ll want to choose a platform that offers both end-to-end encryption and contact key verification. Some platforms offer automatic verification, which can be more convenient, while others rely on manual processes, which can provide a higher level of security.
5. Use Cases for Contact Key Verification
Contact key verification isn’t just for tech enthusiasts. It has practical applications in various scenarios, offering enhanced security and peace of mind.
5.1. Secure Business Communications
Businesses can use contact key verification to secure sensitive communications between employees and clients, preventing data breaches and maintaining confidentiality.
In the business world, data breaches can be incredibly costly, both financially and reputationally. Contact key verification provides a way to secure sensitive communications between employees and clients, reducing the risk of data breaches and maintaining confidentiality. This is especially important for businesses that handle sensitive information, such as financial data, medical records, or legal documents.
5.2. Protecting Personal Information
Individuals can use contact key verification to protect their personal information from phishing attacks and identity theft.
Phishing attacks and identity theft are becoming increasingly common. Contact key verification provides a way to protect your personal information by ensuring that you are communicating with the right people. This can help to prevent you from falling victim to scams and identity theft.
5.3. Securing Financial Transactions
Verifying contacts before conducting financial transactions can prevent fraud and ensure that money is sent to the correct recipient.
Financial transactions are a prime target for fraudsters. Contact key verification can help to secure financial transactions by ensuring that you are sending money to the correct recipient. This can help to prevent fraud and protect your financial assets.
5.4. Ensuring Confidential Medical Consultations
Healthcare professionals can use contact key verification to ensure that medical consultations remain confidential and secure.
Confidentiality is crucial in the healthcare industry. Contact key verification can help healthcare professionals ensure that medical consultations remain confidential and secure. This is especially important when discussing sensitive medical information with patients.
5.5. Government and Diplomatic Communications
Governments and diplomatic organizations can use contact key verification to secure sensitive communications and prevent espionage.
Governments and diplomatic organizations handle highly sensitive information that needs to be protected from espionage. Contact key verification provides a way to secure these communications and prevent unauthorized access. This is crucial for maintaining national security and diplomatic relations.
6. Common Misconceptions About Contact Key Verification
Despite its benefits, several misconceptions surround contact key verification. Let’s debunk some of the most common ones:
6.1. “It’s Too Complicated to Use”
While it may sound technical, most platforms have simplified the process, making it user-friendly for non-technical individuals.
Many people believe that contact key verification is too complicated to use. However, most platforms have simplified the process, making it user-friendly for non-technical individuals. The verification process typically involves comparing a unique code, which is a simple and straightforward task.
6.2. “End-to-End Encryption Is Enough”
End-to-end encryption protects the content of your messages, but it doesn’t verify the identity of the person you’re communicating with. Contact key verification adds an extra layer of security by ensuring you’re talking to the intended recipient.
End-to-end encryption is a valuable security feature, but it’s not enough on its own. While it protects the content of your messages, it doesn’t verify the identity of the person you’re communicating with. Contact key verification adds an extra layer of security by ensuring that you are actually talking to the intended recipient.
6.3. “It Slows Down Communication”
The verification process is usually quick and only needs to be done once per contact, making it a minor inconvenience for a significant security boost.
Some people worry that contact key verification will slow down communication. However, the verification process is usually quick and only needs to be done once per contact. Once a contact is verified, all future communications with that contact will be secure. The minor inconvenience of the initial verification is well worth the significant security boost it provides.
6.4. “It’s Only for Criminals and Activists”
Contact key verification is beneficial for anyone who wants to secure their digital communications, regardless of their profession or activities.
Contact key verification is often associated with criminals and activists who want to protect their communications from law enforcement. However, it’s beneficial for anyone who wants to secure their digital communications, regardless of their profession or activities. Whether you’re a business professional, a healthcare provider, or a private individual, contact key verification can help to protect your sensitive information.
6.5. “It Guarantees 100% Security”
While it significantly enhances security, contact key verification is not foolproof. It protects against specific types of attacks, but it’s essential to maintain other security best practices as well.
While contact key verification significantly enhances security, it’s not a silver bullet. It protects against specific types of attacks, such as man-in-the-middle attacks, but it’s essential to maintain other security best practices as well. This includes using strong passwords, keeping your software up to date, and being cautious of phishing scams.
7. Best Practices for Using Contact Key Verification
To maximize the benefits of contact key verification, follow these best practices:
7.1. Always Verify New Contacts
Whenever you start communicating with someone new, take the time to verify their contact key. This ensures that you’re talking to the right person from the start.
Verifying new contacts is crucial for preventing impersonation attacks. Whenever you start communicating with someone new, take the time to verify their contact key. This ensures that you are talking to the right person from the start and that your communications are secure.
7.2. Use Secure Channels for Verification
When comparing verification codes, use a secure channel such as a phone call or in-person meeting to avoid interception.
When comparing verification codes, it’s important to use a secure channel to avoid interception. This means avoiding insecure channels like email or text message. Instead, use a phone call or in-person meeting to compare the codes. This will help to ensure that the verification process is secure and that you are communicating with the right person.
7.3. Regularly Check Verification Status
Periodically check the verification status of your contacts to ensure their keys haven’t changed, which could indicate a potential security issue.
Contact keys can change for various reasons, such as when a contact gets a new phone or re-installs their messaging app. It’s important to regularly check the verification status of your contacts to make sure that their keys haven’t changed. If a key has changed, you should re-verify the contact to ensure that you are still communicating with the right person.
7.4. Educate Your Contacts
Encourage your contacts to enable contact key verification and understand its importance. The more people who use it, the more secure everyone’s communications become.
The more people who use contact key verification, the more secure everyone’s communications become. Encourage your contacts to enable contact key verification and understand its importance. This will help to create a more secure communication environment for everyone.
7.5. Stay Informed About Security Updates
Keep up-to-date with the latest security updates and best practices for your messaging platforms to ensure you’re using contact key verification effectively.
Security threats are constantly evolving. It’s important to stay informed about the latest security updates and best practices for your messaging platforms to ensure that you are using contact key verification effectively. This will help you to protect your communications from the latest threats.
8. The Future of Contact Key Verification
As digital communication continues to evolve, so will contact key verification. Here are some potential future trends:
8.1. Wider Adoption Across Platforms
More messaging platforms are likely to integrate contact key verification as users become more aware of its benefits.
As users become more aware of the benefits of contact key verification, more messaging platforms are likely to integrate it into their systems. This will make it easier for people to secure their communications and protect their personal information.
8.2. Automated Verification Processes
Future implementations may include automated verification processes that use biometric data or other methods to streamline the verification process.
Manual verification can be time-consuming and inconvenient. Future implementations may include automated verification processes that use biometric data or other methods to streamline the process. This could make contact key verification more accessible and user-friendly.
8.3. Integration with Digital Identity Systems
Contact key verification may become integrated with broader digital identity systems, providing a more seamless and secure way to manage digital identities.
Digital identity systems are becoming increasingly important in today’s digital world. Contact key verification may become integrated with these systems, providing a more seamless and secure way to manage digital identities. This could help to prevent identity theft and fraud.
8.4. Enhanced User Education
Greater emphasis will be placed on educating users about the importance of contact key verification and how to use it effectively.
User education is crucial for the success of contact key verification. Greater emphasis will be placed on educating users about the importance of contact key verification and how to use it effectively. This will help to increase adoption and improve the overall security of digital communications.
8.5. Regulatory Standards
Governments and regulatory bodies may introduce standards and guidelines for contact key verification to promote its adoption and ensure its effectiveness.
As contact key verification becomes more widespread, governments and regulatory bodies may introduce standards and guidelines to promote its adoption and ensure its effectiveness. This could help to create a more secure and trusted digital environment.
9. Troubleshooting Common Issues
Even with the best practices, you might encounter issues while using contact key verification. Here are some common problems and their solutions:
9.1. Verification Codes Don’t Match
- Problem: The verification codes generated on both devices don’t match.
- Solution: Ensure that both devices are connected to the internet and that the correct contact information is saved. Double-check that you’re comparing the codes in real-time and that neither code has expired.
If the verification codes don’t match, there are several possible reasons. First, make sure that both devices are connected to the internet and that the correct contact information is saved. Then, double-check that you are comparing the codes in real-time and that neither code has expired. If you are still having trouble, try restarting both devices and generating new verification codes.
9.2. Contact Key Has Changed Unexpectedly
- Problem: A contact’s key has changed without any known reason.
- Solution: This could indicate a potential security issue. Contact the person through a different secure channel to confirm whether they initiated the key change. If not, it could be a sign of a man-in-the-middle attack.
If a contact’s key has changed unexpectedly, it could indicate a potential security issue. Contact the person through a different secure channel, such as a phone call or in-person meeting, to confirm whether they initiated the key change. If they did not initiate the key change, it could be a sign of a man-in-the-middle attack. In this case, you should stop communicating with the contact until you can verify their identity.
9.3. Difficulty Enabling Contact Key Verification
- Problem: You’re having trouble enabling contact key verification in your messaging app.
- Solution: Ensure that your app is updated to the latest version and that you meet all the requirements for enabling the feature (e.g., two-factor authentication is enabled). Check the app’s help documentation or support resources for specific instructions.
If you are having trouble enabling contact key verification in your messaging app, make sure that your app is updated to the latest version and that you meet all the requirements for enabling the feature (e.g., two-factor authentication is enabled). Check the app’s help documentation or support resources for specific instructions. If you are still having trouble, contact the app’s support team for assistance.
9.4. Confusion About Public Verification Codes
- Problem: You’re unsure how to use or share your public verification code.
- Solution: Public verification codes are designed to be shared openly. You can post them on social media, your website, or other public channels. Others can then use your public verification code to verify your identity in their messaging app.
Public verification codes are designed to be shared openly. You can post them on social media, your website, or other public channels. Others can then use your public verification code to verify your identity in their messaging app. To use someone else’s public verification code, simply copy and paste the code into your messaging app when prompted.
9.5. Incompatible Devices or Software
- Problem: Contact key verification isn’t working because of incompatible devices or software.
- Solution: Ensure that all devices and software are updated to the latest compatible versions. Older devices or software may not support contact key verification.
Contact key verification may not work if you are using incompatible devices or software. Make sure that all devices and software are updated to the latest compatible versions. Older devices or software may not support contact key verification. If you are still having trouble, try using a different device or software.
10. FAQ About Contact Key Verification
To further clarify any lingering questions, here are some frequently asked questions about contact key verification:
| Question | Answer |
|---|---|
| What is the main purpose of contact key verification? | To ensure that you are communicating with the intended person and not an imposter. |
| Is contact key verification the same as end-to-end encryption? | No. End-to-end encryption protects the content of your messages, while contact key verification verifies the identity of the person you’re communicating with. They complement each other. |
| Do all messaging apps offer contact key verification? | No, but many popular apps like Signal, WhatsApp (as an option), and iMessage (with Contact Key Verification) do. |
| How often should I verify my contacts? | Verify new contacts immediately and periodically check the status of existing contacts. |
| What should I do if a contact’s key changes unexpectedly? | Contact the person through a different secure channel to confirm whether they initiated the key change. If not, it could be a sign of a security issue. |
| Is contact key verification difficult to use? | Most platforms have made the process user-friendly for non-technical individuals. |
| Can contact key verification prevent all types of cyberattacks? | No, it protects against specific types of attacks like man-in-the-middle attacks. It’s essential to maintain other security best practices as well. |
| What are public verification codes? | Codes that you can share openly (e.g., on social media) to allow others to verify your identity. |
| What if the verification codes don’t match? | Ensure both devices are connected to the internet, the correct contact information is saved, and you’re comparing the codes in real-time. |
| Is contact key verification only for sensitive communications? | While particularly useful for sensitive communications, it’s beneficial for anyone who wants to enhance their digital security. |
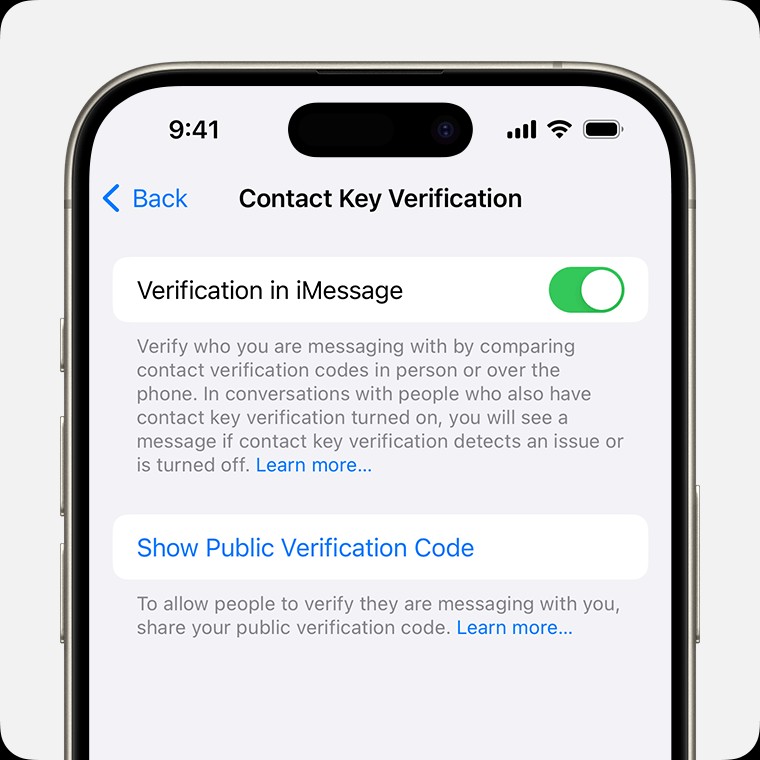 iMessage Contact Key Verification settings
iMessage Contact Key Verification settings
11. Need More Answers? Ask WHAT.EDU.VN!
Still have questions about Contact Key Verification or other tech topics? Don’t hesitate to ask on WHAT.EDU.VN, where you can get free answers and expert advice. Our community is here to help you navigate the digital world with confidence.
11.1. Free and Quick Answers
At WHAT.EDU.VN, we understand that finding answers to your questions can sometimes be a challenge. That’s why we’ve created a platform where you can ask any question and receive free answers quickly. Whether you’re a student, a professional, or simply someone curious about the world, we’re here to help.
11.2. Expert Advice
Our community is made up of experts from various fields who are passionate about sharing their knowledge. When you ask a question on WHAT.EDU.VN, you can be confident that you’ll receive well-informed and accurate answers. Our experts are dedicated to providing you with the best possible advice and guidance.
11.3. Easy to Use Platform
We’ve designed WHAT.EDU.VN to be user-friendly and accessible to everyone. Our platform is easy to navigate, and asking a question is as simple as typing it into the search bar. You can also browse through our extensive library of answered questions to see if your question has already been addressed.
11.4. Get Your Questions Answered Today
Don’t let your questions go unanswered. Visit WHAT.EDU.VN today and get the answers you need to succeed. Our community is waiting to help you navigate the complexities of the digital world. Whether you’re looking for information on technology, science, history, or any other topic, we’ve got you covered.
Stop struggling to find the information you need. With WHAT.EDU.VN, you can ask any question and receive free, expert answers quickly and easily. Join our community today and start learning.
Address: 888 Question City Plaza, Seattle, WA 98101, United States. Whatsapp: +1 (206) 555-7890. Website: WHAT.EDU.VN
Contact Key Verification is a powerful tool for enhancing the security and trustworthiness of your digital communications. By understanding its benefits, implementing best practices, and staying informed about future developments, you can protect yourself from various cyber threats and maintain peace of mind in an increasingly digital world. Remember, for any further questions, what.edu.vn is here to provide you with free and reliable answers.
