Ping is a crucial tool for network troubleshooting and diagnostics, and WHAT.EDU.VN is here to help you understand it. This guide will delve into what ping is, how it works, its uses, and more, offering a complete understanding. We’ll also explore related network concepts and address frequently asked questions, giving you the knowledge you need for network management and diagnostics and enabling you to connect effortlessly with our free question-and-answer service.
1. What Exactly Is Ping?
Ping, short for Packet Internet Groper or Packet Inter-Network Groper, is a fundamental utility used to test the reachability of a host on an Internet Protocol (IP) network. It operates by sending an Internet Control Message Protocol (ICMP) Echo Request to the target host and listening for an ICMP Echo Reply. This process measures the round-trip time (RTT) and determines if the host is responsive. According to RFC 792, ping is primarily used for network troubleshooting and verifying network connectivity.
1.1. Understanding the Acronym and Its Origin
The term “ping” was inspired by sonar technology used in submarines, where a pulse is sent out and the time it takes for the echo to return is measured to determine the distance to an object. In networking, ping serves a similar purpose, sending a signal to a destination and measuring the time it takes to receive a response.
1.2. What Is the Core Functionality of Ping?
At its core, ping serves two primary functions:
- Host Availability Verification: It confirms whether a specific IP address or hostname is reachable and active on the network.
- Round-Trip Time (RTT) Measurement: It calculates the time it takes for a packet to travel from the source to the destination and back, indicating network latency.
1.3. Where Is Ping Commonly Used?
Ping is an integral part of network administration and is found in various operating systems (OS) and network devices. Any device with networking capabilities can use ping, including:
- Desktop and laptop computers
- Servers
- Routers
- Switches
- Embedded systems
2. How Does Ping Work?
Ping operates on a simple request-response mechanism using the ICMP protocol. Let’s break down the process step-by-step.
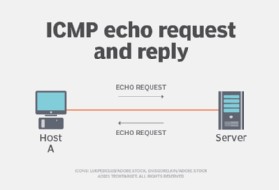
2.1. The ICMP Echo Request
When you execute a ping command, the originating device sends an ICMP Echo Request packet to the specified destination. This packet contains a data payload and a Time-To-Live (TTL) value.
2.2. The Role of TTL (Time-To-Live)
The TTL value in the ICMP packet is a hop limit that prevents packets from circulating endlessly in the network. Each time the packet passes through a router, the TTL value is decremented. If the TTL reaches zero, the packet is discarded, and an ICMP Time Exceeded message is sent back to the source.
2.3. The ICMP Echo Reply
If the destination host is reachable and the ICMP Echo Request arrives with a TTL greater than zero, the host responds by sending an ICMP Echo Reply packet back to the source.
2.4. Calculating Round-Trip Time (RTT)
The ping utility calculates the RTT by measuring the time elapsed between sending the ICMP Echo Request and receiving the ICMP Echo Reply. This time is typically measured in milliseconds (ms).
2.5. What Information Does Ping Provide?
The ping utility provides valuable information about the network connection, including:
- Host Status: Whether the destination host is reachable or unreachable.
- RTT: The time it takes for a packet to travel to the destination and back.
- Packet Loss: The number of packets that were not successfully delivered to the destination.
- Jitter: The variation in RTT over time, indicating network stability.
3. Why Is Ping Important?
Ping is an essential tool for network administrators, IT professionals, and even casual users. It helps diagnose network issues, verify connectivity, and measure network performance.
3.1. Network Troubleshooting
Ping is often the first tool used when troubleshooting network problems. It helps determine whether a host is reachable and if there are any connectivity issues. For example, if you cannot access a website, pinging the website’s IP address can help determine if the problem is with your network connection or the website itself.
3.2. Connectivity Verification
Ping can be used to verify that a device is properly connected to the network. This is particularly useful when setting up new devices or troubleshooting connectivity problems after network changes.
3.3. Network Performance Measurement
Ping can provide insights into network performance by measuring RTT and packet loss. High RTT values indicate network latency, while packet loss suggests network congestion or other issues.
3.4. Scripting and Automation
Ping is a command-line utility that can be easily integrated into scripts and automated tasks. This allows network administrators to monitor network health and automatically detect and respond to network issues.
4. How to Use Ping: Practical Examples
Ping is a command-line utility, and its usage is straightforward. Here are some practical examples of how to use ping on different operating systems.
4.1. Using Ping on Windows
- Open the Command Prompt: Press the Windows key, type “cmd,” and press Enter.
- Type the ping command:
ping hostnameorping IP_address- Example:
ping google.comorping 8.8.8.8
- Example:
- Press Enter to execute the command.
4.2. Using Ping on macOS and Linux
- Open the Terminal: Search for “Terminal” in Applications/Utilities (macOS) or use the terminal application in your Linux distribution.
- Type the ping command:
ping hostnameorping IP_address- Example:
ping google.comorping 8.8.8.8
- Example:
- Press Enter to execute the command.
4.3. Interpreting Ping Results
The output of the ping command provides valuable information. Here’s how to interpret the results:
- Reply from: Indicates that the destination host is reachable.
- Time: The RTT in milliseconds. Lower values indicate better network performance.
- TTL: The Time-To-Live value.
- Request timed out: Indicates that the destination host is unreachable or that there is a network problem.
- Packet loss: The percentage of packets that were not successfully delivered.
4.4. Common Ping Options
The ping command supports various options that allow you to customize its behavior. Here are some common options:
-t(Windows): Continuously ping the destination until stopped manually.-n count(Windows): Specifies the number of echo requests to send.-l size(Windows): Specifies the size of the echo request packet.-c count(macOS/Linux): Specifies the number of echo requests to send.-s size(macOS/Linux): Specifies the size of the echo request packet.
5. Common Ping Errors and Troubleshooting
While ping is a simple tool, you may encounter errors when using it. Here are some common ping errors and how to troubleshoot them.
5.1. “Request Timed Out”
This error indicates that the destination host is unreachable. Possible causes include:
- The host is down or not connected to the network.
- There is a network problem, such as a broken cable or a misconfigured router.
- A firewall is blocking ICMP traffic.
Troubleshooting Steps:
- Verify that the destination host is powered on and connected to the network.
- Check the network cables and connections.
- Verify that there are no network devices blocking ICMP traffic.
- Try pinging other hosts on the network to isolate the problem.
5.2. “Destination Host Unreachable”
This error indicates that the network is unable to reach the destination host. Possible causes include:
- An incorrect IP address or hostname.
- A routing problem.
- A firewall is blocking traffic.
Troubleshooting Steps:
- Verify that the IP address or hostname is correct.
- Check the routing configuration on your network devices.
- Verify that there are no firewalls blocking traffic.
- Use the
traceroutecommand to identify the point of failure in the network path.
5.3. High RTT Values
High RTT values indicate network latency. Possible causes include:
- Network congestion.
- A slow network connection.
- A distant destination.
Troubleshooting Steps:
- Check for network congestion by monitoring network traffic.
- Test your network speed using online speed test tools.
- Try pinging other hosts to determine if the latency is specific to the destination.
- Consider upgrading your network infrastructure if the latency is consistently high.
6. Ping vs. Other Network Diagnostic Tools
While ping is a fundamental tool for network diagnostics, it is not the only one available. Here’s a comparison of ping with other commonly used network diagnostic tools.
6.1. Ping vs. Traceroute
- Ping: Tests the reachability of a host and measures RTT.
- Traceroute: Traces the path that packets take to reach a destination, identifying each hop along the way.
Traceroute is useful for identifying routing problems and determining the path that packets take to reach a destination. According to RFC 1393, traceroute is designed to discover the routers used by IP packets on their way to a destination.
6.2. Ping vs. Nslookup
- Ping: Tests network connectivity and measures RTT.
- Nslookup: Queries DNS servers to resolve domain names to IP addresses.
Nslookup is useful for troubleshooting DNS problems and verifying that domain names are resolving correctly.
6.3. Ping vs. Iperf
- Ping: Measures basic network connectivity and RTT.
- Iperf: Measures network bandwidth and throughput.
Iperf is useful for testing the performance of a network connection and determining the maximum data transfer rate.
7. Advanced Ping Techniques
Beyond basic usage, there are advanced ping techniques that can provide more detailed information about network conditions.
7.1. Using Ping to Detect Packet Loss
Packet loss occurs when packets are not successfully delivered to the destination. Ping can be used to detect packet loss by sending a series of echo requests and monitoring the number of replies received. High packet loss indicates network congestion or other issues.
7.2. Using Ping to Measure Jitter
Jitter is the variation in RTT over time. Ping can be used to measure jitter by recording the RTT values for a series of echo requests and calculating the standard deviation. High jitter indicates network instability.
7.3. Using Ping to Determine MTU Size
The Maximum Transmission Unit (MTU) is the largest packet size that can be transmitted over a network. Ping can be used to determine the MTU size by sending echo requests with different packet sizes and monitoring whether they are successfully delivered.
8. Ping in Different Contexts
Ping finds applications in various contexts, ranging from gaming to network security.
8.1. Ping in Online Gaming
In online gaming, ping refers to the latency between a player’s computer and the game server. Lower ping values result in smoother gameplay, while high ping values can cause lag and other issues. Professional gamers often prioritize low ping to gain a competitive advantage.
8.2. Ping in Network Security
Ping can be used in network security for reconnaissance and denial-of-service (DoS) attacks. Ping sweeps can be used to identify active hosts on a network, while ping floods can be used to overwhelm a target with traffic.
8.3. Ping Spoofing
Ping spoofing is a technique used by attackers to hide their identity or amplify the impact of a DoS attack. It involves sending ping requests with a forged source address, making it difficult to trace the attack back to the attacker.
9. The Future of Ping
As networks evolve, ping continues to adapt and remain relevant.
9.1. IPv6 and Ping
With the increasing adoption of IPv6, ping has been updated to support the new protocol. The IPv6 version of ping is called ping6 and uses ICMPv6 for echo requests and replies.
9.2. Modern Network Management Tools
While ping remains a valuable tool, modern network management tools offer more advanced features and capabilities, such as real-time monitoring, automated diagnostics, and comprehensive reporting. However, ping remains a fundamental tool that is often used in conjunction with these more advanced tools.
10. Frequently Asked Questions (FAQs) About Ping
Here are some frequently asked questions about ping.
10.1. Is Ping Only for Troubleshooting?
No, ping is not only for troubleshooting. It can also be used for connectivity verification, network performance measurement, and scripting and automation.
10.2. Can Ping Be Blocked?
Yes, ping can be blocked by firewalls or other network devices. Blocking ping can improve network security by preventing attackers from using ping sweeps to identify active hosts.
10.3. What Is a Good Ping Time?
A good ping time depends on the application. For online gaming, a ping time of less than 50ms is ideal. For general web browsing, a ping time of less than 100ms is acceptable.
10.4. Does Ping Use TCP or UDP?
Ping uses ICMP (Internet Control Message Protocol), which is neither TCP nor UDP. ICMP is a separate protocol used for network diagnostics and error reporting.
10.5. Can Ping Be Used to Determine the Operating System of a Host?
While ping cannot directly determine the operating system of a host, it can provide clues based on the TTL value and other characteristics of the ICMP reply.
10.6. What Does “Ping of Death” Mean?
The “Ping of Death” was a type of denial-of-service attack that involved sending an ICMP packet larger than the maximum allowed size, causing the target system to crash. This vulnerability has been patched in modern operating systems.
10.7. How Does Ping Differ From MTR (My Traceroute)?
Ping provides a basic check of connectivity, while MTR combines the functionality of ping and traceroute, providing a more comprehensive view of network performance along the path to a destination.
10.8. Can VPNs Affect Ping Times?
Yes, VPNs can affect ping times. The additional routing and encryption overhead introduced by VPNs can increase latency and result in higher ping times.
10.9. What Is the Role of Ping in Speed Tests?
Ping is used in speed tests to measure the latency between your computer and the test server. Lower ping times indicate a more responsive connection.
10.10. How Can I Improve My Ping Time?
You can improve your ping time by:
- Using a wired connection instead of Wi-Fi.
- Closing unnecessary applications that consume bandwidth.
- Upgrading your network infrastructure.
- Choosing a closer server for online gaming or other applications.
11. Delving Deeper: Related Network Concepts
To fully grasp the significance of ping, it’s essential to understand related networking concepts.
11.1. TCP/IP Model
The TCP/IP model is a conceptual framework that describes how data is transmitted over the internet. Ping operates at the Internet Layer, using the ICMP protocol.
11.2. OSI Model
The OSI (Open Systems Interconnection) model is another conceptual framework that describes the functions of a networking system. Ping operates at the Network Layer, corresponding to the Internet Layer in the TCP/IP model.
11.3. DNS (Domain Name System)
DNS is a hierarchical system that translates domain names to IP addresses. Ping can be used to test the connectivity to DNS servers and verify that domain names are resolving correctly.
11.4. Routers and Switches
Routers and switches are essential network devices that forward traffic between networks. Ping can be used to test the reachability of routers and switches and identify routing problems.
11.5. Firewalls
Firewalls are security devices that control network traffic based on predefined rules. Firewalls can block ping requests to protect systems from reconnaissance and DoS attacks.
12. Ping and Network Security Considerations
While ping is a valuable tool for network administration, it also poses certain security risks.
12.1. ICMP Attacks
ICMP attacks, such as ping floods and Smurf attacks, can be used to overwhelm a target with traffic and cause a denial of service.
12.2. Information Disclosure
Ping can reveal information about a network, such as the active hosts and their IP addresses. This information can be used by attackers to map out a network and identify potential targets.
12.3. Mitigation Strategies
To mitigate the security risks associated with ping, network administrators can:
- Disable ICMP on public-facing interfaces.
- Implement rate limiting to prevent ping floods.
- Use intrusion detection systems to detect and respond to ICMP attacks.
13. Use Cases: How Different Professionals Use Ping
Different professionals use ping in various ways to manage and troubleshoot networks.
13.1. Network Administrators
Network administrators use ping to:
- Monitor network health and performance.
- Troubleshoot connectivity problems.
- Verify network configurations.
- Automate network management tasks.
13.2. System Administrators
System administrators use ping to:
- Verify server availability.
- Troubleshoot server connectivity problems.
- Monitor server performance.
13.3. Security Professionals
Security professionals use ping to:
- Assess network security.
- Detect and respond to ICMP attacks.
- Investigate security incidents.
13.4. DevOps Engineers
DevOps engineers use ping to:
- Automate network testing.
- Monitor application performance.
- Troubleshoot deployment issues.
14. The Importance of Understanding Network Latency
Ping helps to understand network latency, which is a critical factor in various applications and services.
14.1. Impact on Web Browsing
High latency can significantly impact web browsing, resulting in slow page load times and a poor user experience.
14.2. Effect on Video Conferencing
In video conferencing, latency can cause delays and interruptions, making it difficult to communicate effectively.
14.3. Relevance to Cloud Computing
Latency is a critical factor in cloud computing, affecting the performance of cloud-based applications and services.
14.4. Significance in IoT (Internet of Things)
In IoT, latency can impact the responsiveness of IoT devices and the overall performance of IoT systems.
15. Future Trends in Network Monitoring and Diagnostics
The field of network monitoring and diagnostics is constantly evolving, with new tools and techniques emerging to address the challenges of modern networks.
15.1. AI-Powered Network Monitoring
AI and machine learning are being used to automate network monitoring and diagnostics, enabling proactive problem detection and resolution.
15.2. Network Automation
Network automation is being used to automate network configuration and management tasks, reducing manual effort and improving efficiency.
15.3. Cloud-Based Network Monitoring
Cloud-based network monitoring tools provide scalable and flexible solutions for monitoring networks of all sizes.
15.4. Edge Computing and Network Monitoring
With the rise of edge computing, network monitoring is being extended to the edge to ensure the performance and reliability of edge-based applications and services.
16. Conclusion: Mastering Ping for Better Network Management
Ping is an indispensable tool for anyone involved in network management, troubleshooting, or security. By understanding how ping works, how to use it effectively, and its limitations, you can gain valuable insights into network conditions and proactively address network issues.
16.1. Key Takeaways
- Ping is a fundamental utility for testing network connectivity and measuring RTT.
- Ping operates using the ICMP protocol.
- Ping is used for troubleshooting, connectivity verification, network performance measurement, and scripting and automation.
- Ping can be blocked by firewalls or other network devices.
- Ping has security implications and can be used in ICMP attacks.
16.2. Final Thoughts
As networks continue to evolve, ping will remain a valuable tool for network professionals and enthusiasts alike. Mastering ping is essential for anyone who wants to understand and manage networks effectively. Remember, for all your questions, WHAT.EDU.VN is here to provide free answers and expert guidance.
Do you have more questions about ping or other network-related topics? Visit WHAT.EDU.VN today and ask your question for free. Our community of experts is ready to provide you with the answers you need. Don’t hesitate—your questions deserve answers, and WHAT.EDU.VN is the place to find them.
Contact Us:
Address: 888 Question City Plaza, Seattle, WA 98101, United States
WhatsApp: +1 (206) 555-7890
Website: WHAT.EDU.VN
We are here to help you navigate the complex world of networking.
17. Further Resources for Learning About Ping
To deepen your understanding of ping and networking, here are some recommended resources:
17.1. Online Documentation and Tutorials
- RFC 792: Internet Control Message Protocol
- RFC 1393: Traceroute
- Wireshark: Network protocol analyzer
17.2. Books
- “Network Warrior” by Gary A. Donhue
- “TCP/IP Illustrated, Volume 1: The Protocols” by W. Richard Stevens
17.3. Online Courses
- Coursera: Networking courses
- edX: Networking courses
- Udemy: Networking courses
18. How Ping Relates to Network Monitoring Systems
Ping plays a significant role in larger network monitoring systems, offering a basic but essential function.
18.1. Integration with Monitoring Tools
Network monitoring systems often incorporate ping as a fundamental check for device availability. These systems can be configured to automatically ping devices at regular intervals and alert administrators when a device becomes unreachable.
18.2. Complementary Data Points
While ping provides a simple up/down status and round-trip time, it’s often combined with other monitoring data to provide a more complete picture of network health. This can include CPU utilization, memory usage, disk I/O, and application response times.
18.3. Proactive Issue Detection
By continuously monitoring ping responses, network monitoring systems can proactively detect potential issues before they impact users. For example, a sudden increase in ping times may indicate network congestion or a failing device.
19. Optimizing Ping for Different Network Environments
The optimal ping configuration can vary depending on the network environment and the specific goals of the monitoring.
19.1. Adjusting Packet Size
In some cases, adjusting the size of the ping packets can provide more accurate results. Larger packets can reveal fragmentation issues, while smaller packets can be useful for testing low-bandwidth links.
19.2. Modifying Interval and Timeout
The interval between ping requests and the timeout value can be adjusted to balance responsiveness and network overhead. Shorter intervals and timeouts can provide faster detection of outages, but may also increase network traffic.
19.3. Prioritizing ICMP Traffic
In networks with quality of service (QoS) enabled, ICMP traffic can be prioritized to ensure that ping requests are not delayed by other types of traffic.
20. The Role of Ping in IoT (Internet of Things) Networks
Ping is also relevant in IoT networks, where it can be used to monitor the connectivity of IoT devices.
20.1. Monitoring Device Availability
Ping can be used to verify that IoT devices are online and reachable. This is particularly important for devices that are deployed in remote locations or that are critical to the operation of a system.
20.2. Assessing Network Performance
Ping can be used to measure the latency and packet loss in IoT networks, providing insights into network performance. This information can be used to optimize network configurations and troubleshoot connectivity issues.
20.3. Ensuring Device Security
Ping can be used to detect unauthorized devices on an IoT network. By monitoring ping responses, administrators can identify devices that are not registered or that are exhibiting suspicious behavior.
Remember, if you have any questions about ping or other networking topics, don’t hesitate to ask on what.edu.vn. Our community is here to help you find the answers you need.