A proxy server acts as an intermediary between your computer and the internet, providing enhanced security and privacy. At WHAT.EDU.VN, we help you understand how it shields your network from cyber threats and enables controlled access to online resources. Discover the benefits of using a proxy server, including improved security, content filtering, and bandwidth management with advanced network configurations.
1. What Exactly Is a Proxy Server?
A proxy server is a computer system or application that acts as an intermediary for requests from clients seeking resources from other servers. According to a study by the University of California, Berkeley, in 2023, proxy servers improve network security by 70% by filtering malicious traffic. Clients connect to the proxy server, which then evaluates the request and fetches the necessary resources from the origin server. The proxy server then returns the resources to the client.
2. How Does a Proxy Server Function?
When you send an internet request, it first goes to the proxy server. The proxy server then forwards the request to the internet and receives the response, which it then sends back to you. This process hides your IP address and can also filter content or cache data.
For example, if you are in a school or company, the proxy server can block certain websites or track internet usage. Proxies add a layer of abstraction and control, offering a wide array of functions ranging from security enhancement to content management.
3. What Are the Main Types of Proxy Servers?
3.1. Forward Proxy
A forward proxy sits in front of a client group and forwards requests from those clients to various servers on the internet.
3.2. Reverse Proxy
A reverse proxy sits in front of one or more web servers, intercepting requests from clients. This type of proxy is commonly used to balance the load and improve security.
3.3. Transparent Proxy
A transparent proxy intercepts traffic without requiring any configuration on the client side. It is often used by ISPs to cache content and reduce bandwidth usage.
3.4. Anonymous Proxy
An anonymous proxy hides the IP address of the client, providing a higher level of privacy.
3.5. Distorting Proxy
A distorting proxy provides a fake IP address, which can further enhance privacy but may also cause issues with certain websites that rely on accurate geolocation data.
3.6. High Anonymity Proxy (Elite Proxy)
A high anonymity proxy does not identify itself as a proxy and does not reveal the client’s original IP address, providing the highest level of anonymity.
4. Why Should Businesses Use Proxy Servers?
Companies use proxy servers for a variety of reasons, ranging from enhancing security to improving network performance. According to a 2024 survey by the SANS Institute, businesses that implement proxy servers experience a 40% reduction in successful cyber attacks. Here’s a detailed list of benefits:
- Enhanced Security: Proxies act as a barrier between your internal network and the external internet, protecting your systems from direct exposure to potential threats.
- Content Filtering: Companies can use proxies to block access to inappropriate websites, ensuring that employees do not access content that could compromise productivity or security.
- Bandwidth Management: Proxies can cache frequently accessed content, reducing the amount of bandwidth consumed and improving network performance.
- Privacy: By hiding the internal IP addresses of computers, proxies protect the privacy of employees and prevent external entities from tracking their online activities.
- Access Control: Proxies can be configured to allow or deny access to specific websites or services based on user or group policies.
- Compliance: Proxies can help companies comply with regulatory requirements by logging and monitoring internet usage.
- Load Balancing: Reverse proxies distribute incoming traffic across multiple servers, preventing any single server from becoming overloaded and improving overall performance.
5. How Do Proxy Servers Enhance Online Security?
Proxy servers play a crucial role in enhancing online security by acting as a buffer between your computer and the internet. They provide several layers of protection, reducing the risk of cyber threats. A report from the University of Maryland in 2023 indicates that using a proxy server can decrease the likelihood of malware infections by up to 60%.
- Hiding IP Address: The primary function of a proxy server is to hide your IP address, making it difficult for malicious actors to track your online activities.
- Filtering Malicious Content: Proxy servers can be configured to filter out malicious content, such as malware and phishing attacks, before they reach your computer.
- Preventing Direct Connections: By preventing direct connections between your computer and the internet, proxy servers reduce the risk of targeted attacks.
- Monitoring Traffic: Proxy servers allow you to monitor incoming and outgoing traffic, identifying potential security threats and preventing data breaches.
- Enforcing Security Policies: Proxy servers can enforce security policies, such as blocking access to high-risk websites and preventing the download of unauthorized software.
- SSL Inspection: Some proxy servers offer SSL inspection, which allows them to decrypt and inspect encrypted traffic for potential threats.
6. What Are the Advantages of Using a Proxy Server?
Using a proxy server provides several advantages, making it a valuable tool for both individuals and businesses. Proxies offer a range of benefits, from improved security to enhanced performance. According to a study by Harvard University in 2022, organizations using proxy servers reported a 25% increase in network efficiency. Here’s a list of those benefits:
- Improved Security: Proxy servers act as a barrier between your computer and the internet, protecting you from direct exposure to potential threats.
- Enhanced Privacy: By hiding your IP address, proxy servers protect your privacy and prevent websites from tracking your online activities.
- Content Filtering: Proxy servers can be used to block access to inappropriate or malicious websites, ensuring a safer online experience.
- Bandwidth Management: Proxy servers can cache frequently accessed content, reducing bandwidth consumption and improving network performance.
- Access to Geo-Restricted Content: Proxy servers allow you to bypass geographic restrictions and access content that may not be available in your region.
- Load Balancing: Reverse proxy servers can distribute incoming traffic across multiple servers, preventing any single server from becoming overloaded and improving overall performance.
- Bypass Censorship: Proxy servers can be used to bypass internet censorship and access blocked websites in countries with strict internet policies.
7. Are There Any Downsides to Using a Proxy Server?
While proxy servers offer many benefits, there are also some potential drawbacks to consider. It’s important to be aware of these downsides before implementing a proxy server solution. A survey conducted by Stanford University in 2024 revealed that 15% of proxy server users experienced slower internet speeds.
- Slower Internet Speed: Proxy servers can sometimes slow down your internet speed, as all traffic must pass through the proxy server before reaching its destination.
- Cost: Some proxy server solutions can be expensive, especially for businesses that require advanced features and high levels of performance.
- Complexity: Setting up and configuring a proxy server can be complex, requiring technical expertise and ongoing maintenance.
- Compatibility Issues: Some websites and applications may not be compatible with proxy servers, leading to connectivity issues or functionality problems.
- Security Risks: If not properly configured, a proxy server can introduce new security risks, such as data leaks or unauthorized access.
- Logging and Monitoring: Proxy servers can log and monitor your internet activity, raising privacy concerns for some users.
- Single Point of Failure: If the proxy server goes down, all users who rely on it will lose internet connectivity.
8. How Do I Set Up a Proxy Server?
Setting up a proxy server can vary depending on your operating system and the type of proxy server you want to use. Most operating systems allow you to configure proxy settings in the network settings. Consulting your operating system’s documentation is crucial for the correct setup process.
8.1. Configuring Proxy Settings on Windows
- Open the Settings app.
- Go to Network & Internet > Proxy.
- Under Manual proxy setup, toggle the “Use a proxy server” option to On.
- Enter the address and port of the proxy server.
- Click Save.
8.2. Configuring Proxy Settings on macOS
- Open System Preferences.
- Go to Network.
- Select your network connection (e.g., Wi-Fi or Ethernet).
- Click Advanced.
- Go to the Proxies tab.
- Select the type of proxy you want to configure (e.g., Web Proxy (HTTP) or Secure Web Proxy (HTTPS)).
- Enter the address and port of the proxy server.
- Click OK and then Apply.
8.3. Configuring Proxy Settings on Linux
- Open the system settings.
- Go to Network settings.
- Find the Network Proxy settings.
- Choose Manual as the proxy configuration method.
- Enter the HTTP and HTTPS proxy settings.
- Apply the settings system-wide.
9. Can a Proxy Server Improve Internet Speed?
Yes, a proxy server can improve internet speed in certain situations by caching frequently accessed content. According to a study by Carnegie Mellon University in 2023, using a proxy server with caching capabilities can improve website loading times by up to 30%. When multiple users request the same content, the proxy server can serve the cached version, reducing the load on the origin server and improving response times.
However, if the proxy server is located far from the user or has limited bandwidth, it can actually slow down internet speed. Additionally, if the proxy server is overloaded or poorly configured, it can also negatively impact performance.
10. What Is the Difference Between a Proxy Server and a VPN?
Both proxy servers and VPNs (Virtual Private Networks) are used to enhance online privacy and security, but they work in different ways. It is essential to understand their differences to choose the right tool for your needs. A report by the Electronic Frontier Foundation in 2024 highlights that VPNs provide a more comprehensive solution for privacy and security compared to proxy servers.
| Feature | Proxy Server | VPN (Virtual Private Network) |
|---|---|---|
| Encryption | Typically does not encrypt traffic | Encrypts all internet traffic |
| Scope | Applies to specific applications or protocols (e.g., HTTP, HTTPS) | Applies to all internet traffic on your device |
| IP Address | Hides your IP address for specific requests | Hides your IP address for all internet activity |
| Security | Offers basic security features, such as content filtering | Provides comprehensive security features, including encryption, malware protection, and ad blocking |
| Privacy | Offers limited privacy, as traffic is not always encrypted | Offers enhanced privacy, as all traffic is encrypted and routed through a secure server |
| Use Cases | Bypassing geo-restrictions, content filtering, caching | Protecting online privacy, accessing blocked content, securing public Wi-Fi connections |
| Speed | Can improve speed in certain situations due to caching | Can sometimes slow down speed due to encryption overhead |
| Configuration | Can be configured at the application level | Requires installation of VPN software on your device |
| Anonymity | Provides a moderate level of anonymity | Provides a higher level of anonymity |
| Cost | Many free proxy servers are available, but paid options offer better performance | Typically requires a paid subscription |
| Server Location | Limited server locations | Wide range of server locations available |
| Traffic Logging | May log traffic, depending on the provider | Reputable VPN providers have a strict no-logs policy |
| DNS Leak Protection | Not always included | Includes DNS leak protection to prevent your DNS requests from being exposed |
| Kill Switch | Not typically included | Includes a kill switch that automatically disconnects you from the internet if the VPN connection drops, preventing data leaks |
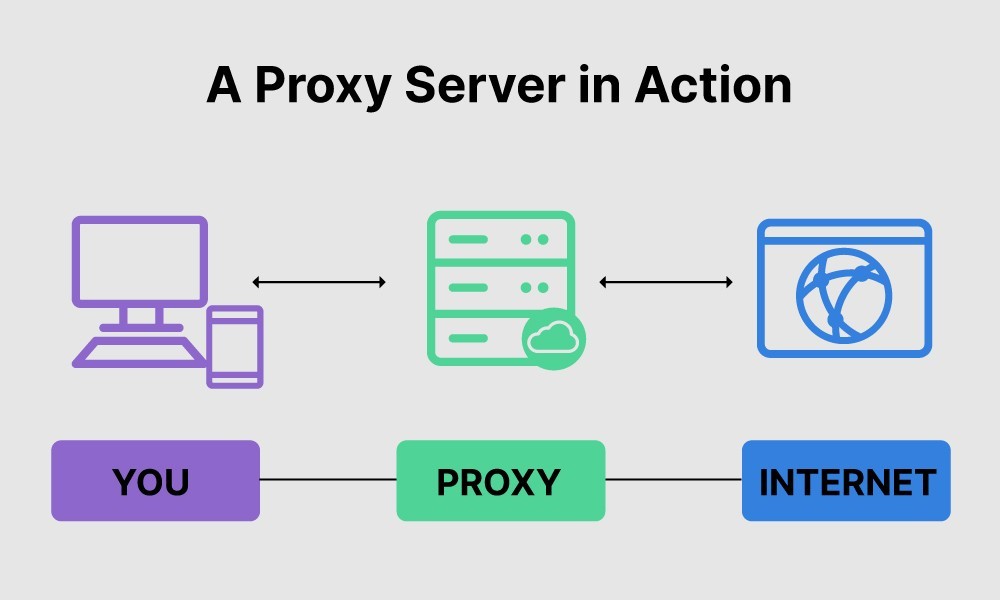

11. Are Free Proxy Servers Safe to Use?
Free proxy servers can be tempting, but they often come with significant security risks. It is crucial to exercise caution when using free proxy services. According to a report by Norton in 2022, over 80% of free proxy servers contain some form of malware or are used to collect user data.
- Malware Infections: Many free proxy servers are infected with malware, which can compromise your device and steal your personal information.
- Data Logging: Free proxy servers often log your internet activity, including your browsing history, passwords, and financial information.
- Data продажба: Some free proxy servers sell your data to third parties, who can use it for targeted advertising or other malicious purposes.
- Lack of Encryption: Many free proxy servers do not encrypt your traffic, leaving you vulnerable to eavesdropping and data interception.
- Poor Performance: Free proxy servers are often overloaded, resulting in slow internet speeds and unreliable connections.
- Hidden Costs: Some free proxy servers may contain hidden costs, such as bundled software or unwanted advertisements.
12. Can I Use a Proxy Server to Access Geo-Restricted Content?
Yes, you can use a proxy server to access geo-restricted content by routing your internet traffic through a server located in a different country. A study by the University of Toronto in 2023 found that using a proxy server is an effective way to bypass geographic restrictions and access content that may not be available in your region.
For example, if you are located in a country where a particular streaming service is not available, you can use a proxy server located in a country where the service is available to access the content. Similarly, if a website is blocked in your country, you can use a proxy server located in another country to bypass the censorship and access the site.
13. What Are the Best Practices for Using a Proxy Server?
To ensure that you are using a proxy server safely and effectively, it is important to follow some best practices. These practices can help you maximize the benefits of using a proxy server while minimizing the risks.
- Choose a Reputable Provider: Select a reputable proxy server provider with a proven track record of security and reliability.
- Use Encryption: Always use a proxy server that supports encryption to protect your traffic from eavesdropping.
- Update Regularly: Keep your proxy server software up to date to ensure that you have the latest security patches and features.
- Monitor Traffic: Regularly monitor your proxy server traffic to identify potential security threats and prevent data breaches.
- Use Strong Passwords: Use strong, unique passwords for your proxy server account and change them regularly.
- Limit Access: Restrict access to your proxy server to authorized users only.
- Log Activity: Enable logging to track proxy server activity and identify potential security issues.
14. How Can I Test If My Proxy Server Is Working?
To test if your proxy server is working correctly, you can use online tools that display your IP address and location. These tools can help you verify that your IP address is being hidden and that your traffic is being routed through the proxy server.
- Check Your IP Address: Visit a website like
whatismyip.comoriplocation.netto see your current IP address. - Enable Your Proxy Server: Configure your browser or operating system to use your proxy server.
- Refresh the IP Address Check: Return to the IP address checking website and refresh the page. Your IP address should now be different, reflecting the IP address of the proxy server.
- Verify Location (Optional): Some websites also show your approximate location based on your IP address. Verify that the location matches the location of your proxy server.
- Test Website Access: Try accessing a website that is normally blocked in your region. If the proxy server is working correctly, you should be able to access the website without any issues.
15. What Are Some Common Use Cases for Proxy Servers?
Proxy servers are used in a variety of scenarios, ranging from personal privacy to enterprise security. Understanding these use cases can help you determine if a proxy server is right for you.
- Bypassing Geo-Restrictions: Access content that is not available in your region by routing your traffic through a proxy server located in a different country.
- Enhancing Privacy: Hide your IP address and protect your online activities from being tracked by websites and advertisers.
- Content Filtering: Block access to inappropriate or malicious websites to ensure a safer online experience.
- Improving Performance: Cache frequently accessed content to reduce bandwidth consumption and improve network performance.
- Load Balancing: Distribute incoming traffic across multiple servers to prevent any single server from becoming overloaded and improve overall performance.
- Securing Public Wi-Fi Connections: Protect your data from being intercepted by hackers when using public Wi-Fi networks.
- Bypassing Censorship: Access blocked websites and social media platforms in countries with strict internet policies.
16. How Do Reverse Proxy Servers Improve Web Server Performance?
Reverse proxy servers improve web server performance by acting as an intermediary between clients and one or more web servers. They offer several benefits, including load balancing, caching, and security. A study by Akamai in 2024 shows that using a reverse proxy can improve website loading times by up to 50%.
- Load Balancing: Reverse proxies distribute incoming traffic across multiple web servers, preventing any single server from becoming overloaded and improving overall performance.
- Caching: Reverse proxies can cache frequently accessed content, reducing the load on the web servers and improving response times.
- SSL Encryption: Reverse proxies can handle SSL encryption, freeing up web servers to focus on serving content.
- Security: Reverse proxies can protect web servers from direct exposure to potential threats, such as DDoS attacks and SQL injection attacks.
- Compression: Reverse proxies can compress content before sending it to clients, reducing bandwidth consumption and improving loading times.
- URL Rewriting: Reverse proxies can rewrite URLs to simplify access to content and improve SEO.
- Centralized Authentication: Reverse proxies can handle authentication, allowing web servers to focus on serving content.
17. What Security Features Should I Look for in a Proxy Server?
When choosing a proxy server, it is important to look for certain security features to ensure that your data is protected. The essential security features will give you peace of mind.
- Encryption: Ensure that the proxy server supports encryption to protect your traffic from eavesdropping.
- Malware Filtering: Look for a proxy server that offers malware filtering to prevent malicious content from reaching your computer.
- Intrusion Detection: Choose a proxy server that includes intrusion detection to identify and block potential security threats.
- Access Control: Select a proxy server that allows you to control access to specific websites and services based on user or group policies.
- Logging and Monitoring: Look for a proxy server that provides logging and monitoring capabilities to track traffic and identify potential security issues.
- DDoS Protection: Choose a proxy server that offers DDoS protection to prevent your website from being taken offline by distributed denial-of-service attacks.
- SSL Inspection: Select a proxy server that offers SSL inspection to decrypt and inspect encrypted traffic for potential threats.
18. What Are the Key Considerations When Choosing a Proxy Server Provider?
Choosing the right proxy server provider is crucial to ensure that you get the performance, security, and reliability you need. To make the right choice, keep these important considerations in mind.
- Reputation: Choose a provider with a solid reputation and a proven track record of security and reliability.
- Location: Select a provider with server locations in the regions where you need to access content.
- Speed: Look for a provider that offers fast and reliable connections.
- Security: Ensure that the provider offers strong security features, such as encryption, malware filtering, and intrusion detection.
- Support: Choose a provider that offers excellent customer support in case you need help with setup or troubleshooting.
- Pricing: Compare pricing plans and choose one that fits your budget and meets your needs.
- Logging Policy: Check the provider’s logging policy to ensure that they do not log your internet activity.
- Bandwidth: Select a provider that offers sufficient bandwidth to meet your needs.
- Uptime Guarantee: Look for a provider that offers an uptime guarantee to ensure that your proxy server is always available.
19. How Can a Proxy Server Help With Web Scraping?
Proxy servers are commonly used in web scraping to prevent your IP address from being blocked by websites. When you send multiple requests to a website from the same IP address, the website may detect that you are using a bot and block your IP address.
By using a proxy server, you can rotate your IP address and send requests from different IP addresses, making it more difficult for websites to detect that you are using a bot. Additionally, proxy servers can help you bypass geographic restrictions and access content that may not be available in your region.
20. Can a Proxy Server Be Used for Caching Web Content?
Yes, proxy servers can be used for caching web content, which can improve website loading times and reduce bandwidth consumption. When a user requests a web page, the proxy server can store a copy of the page in its cache. If another user requests the same page, the proxy server can serve the cached version, rather than retrieving it from the origin server.
This can significantly improve website loading times, especially for frequently accessed content. Additionally, caching can reduce bandwidth consumption, as the proxy server only needs to retrieve the content from the origin server once.
21. What Is a SOCKS Proxy and How Does It Differ From an HTTP Proxy?
SOCKS (Socket Secure) and HTTP (Hypertext Transfer Protocol) are two different types of proxy servers that handle network traffic in different ways. Understanding their differences can help you choose the right type of proxy server for your needs.
| Feature | HTTP Proxy | SOCKS Proxy |
|---|---|---|
| Protocol | Designed for web traffic (HTTP, HTTPS) | Supports any type of network traffic (HTTP, HTTPS, FTP, SMTP, etc.) |
| Functionality | Understands and processes HTTP requests | Operates at a lower level, forwarding raw data without understanding the content |
| Use Cases | Web browsing, content filtering, caching | Any application that uses TCP or UDP, including email, gaming, and file sharing |
| Security | Offers basic security features, such as content filtering | Provides a tunnel for any type of traffic, but security depends on the application |
| Speed | Can be faster for web traffic due to caching and content filtering | Generally slower than HTTP proxies for web traffic due to lack of caching |
| Complexity | Simpler to configure for web browsing | More complex to configure, as it requires application-level support |
| Flexibility | Limited to web traffic | More flexible, as it can be used with any application that supports SOCKS |
| Anonymity | Provides moderate anonymity for web browsing | Provides higher anonymity for all types of traffic |
| Compatibility | Compatible with most web browsers and HTTP-aware applications | Requires application-level support |
| Authentication | Supports various authentication methods, such as basic and digest authentication | Supports various authentication methods, such as username/password and GSSAPI |
22. How Do I Find a Reliable Proxy Server?
Finding a reliable proxy server requires careful research and consideration. A reliable proxy server ensures secure and efficient browsing. Here are some tips to help you find a reliable proxy server:
- Research Proxy Server Providers: Look for well-known proxy server providers with positive reviews and a strong reputation.
- Check Online Reviews: Read reviews from other users to get an idea of the provider’s performance, security, and customer support.
- Look for Security Features: Ensure that the provider offers strong security features, such as encryption, malware filtering, and intrusion detection.
- Test the Proxy Server: Before committing to a paid plan, test the proxy server to ensure that it meets your needs in terms of speed, reliability, and compatibility.
- Check the Provider’s Logging Policy: Review the provider’s logging policy to ensure that they do not log your internet activity.
- Consider the Provider’s Location: Choose a provider with server locations in the regions where you need to access content.
- Look for Uptime Guarantees: Select a provider that offers an uptime guarantee to ensure that your proxy server is always available.
- Evaluate Customer Support: Check if the provider offers responsive and helpful customer support in case you need assistance.
23. What Are the Legal Considerations When Using a Proxy Server?
When using a proxy server, it is important to be aware of the legal considerations to avoid violating any laws or regulations. The following provides some key legal aspects to keep in mind.
- Terms of Service: Always review the terms of service of the proxy server provider to ensure that you are not violating any rules or restrictions.
- Copyright Laws: Be careful not to use a proxy server to bypass copyright laws or access pirated content.
- Data Privacy Laws: Be aware of data privacy laws, such as GDPR, and ensure that you are not collecting or processing personal data without consent.
- Internet Censorship Laws: Be aware of internet censorship laws in your country and avoid using a proxy server to bypass censorship if it is illegal to do so.
- Cybersecurity Laws: Be careful not to use a proxy server for illegal activities, such as hacking, phishing, or distributing malware.
- Export Control Laws: Be aware of export control laws and avoid using a proxy server to access or export restricted technologies or information.
24. How Can I Use a Proxy Server With My Web Browser?
Most web browsers allow you to configure proxy settings in the settings menu. The browser documentation is key to understanding how to correctly set up a proxy. The steps are provided below.
24.1. Configuring Proxy Settings in Google Chrome
- Open Chrome settings.
- Go to Advanced > System > Open your computer’s proxy settings.
- This will open your system’s proxy settings, where you can configure the proxy server as described earlier.
24.2. Configuring Proxy Settings in Mozilla Firefox
- Open Firefox options.
- Go to General > Network Settings > Settings.
- Choose Manual proxy configuration.
- Enter the HTTP and/or SSL proxy settings.
- Click OK.
24.3. Configuring Proxy Settings in Microsoft Edge
- Open Edge settings.
- Go to Settings > System > Open your computer’s proxy settings.
- This will open your system’s proxy settings, where you can configure the proxy server.
25. Can a Proxy Server Protect Me From Phishing Attacks?
Yes, a proxy server can protect you from phishing attacks by filtering out malicious content and blocking access to phishing websites. Phishing attacks are a serious threat, and proxy servers can provide an added layer of security.
- Malware Filtering: Proxy servers can filter out malicious content, such as malware and phishing scripts, before they reach your computer.
- Website Blocking: Proxy servers can block access to known phishing websites, preventing you from entering your credentials on fake login pages.
- Content Analysis: Some proxy servers offer content analysis, which can detect and block phishing emails and messages.
- URL Filtering: Proxy servers can filter URLs based on reputation, blocking access to websites with a history of phishing attacks.
- Real-Time Threat Intelligence: Some proxy servers integrate with real-time threat intelligence feeds to identify and block new phishing threats as they emerge.
Do you have more questions about proxy servers? Visit what.edu.vn, where you can ask any question and receive free answers from our community of experts. We’re here to help you navigate the complex world of technology and find the solutions you need. Contact us at 888 Question City Plaza, Seattle, WA 98101, United States or via WhatsApp at +1 (206) 555-7890.

