Tailgating is a physical security breach where an unauthorized individual gains access to secure areas by following an authorized person. This article from WHAT.EDU.VN explores tailgating, its dangers, and how to prevent it. Learn about access control, security measures and best practices for protection against unauthorized access and potential data breaches.
1. What Is Tailgating in Physical Security?
Tailgating, also known as piggybacking, refers to a physical security breach. It occurs when an unauthorized person (UP) gains entry to a secured area by following an authorized person (AP) without proper authorization or detection by security systems. This bypasses access controls, putting organizations at risk.
2. How Does Tailgating Work as a Security Threat?
Tailgating exploits human behavior and security vulnerabilities. It often relies on:
- Human Carelessness: Authorized individuals may not be vigilant about who they allow to follow them.
- Ingenuity and Confidence: Unauthorized individuals can use social engineering tactics to appear legitimate or create a sense of urgency.
- Exploiting Cognitive Biases: Attackers take advantage of our tendency to be courteous, trusting, or simply habitual.
3. What Are the Common Methods Used in Tailgating Attacks?
Tailgating attacks come in various forms:
- Following Through a Door: The most basic method, where someone simply walks behind an authorized person.
- Exploiting Unclosed Doors: Entering after an authorized person leaves a door ajar.
- Propping Doors Open: Taking advantage of doors left open for ventilation or convenience.
- Disguise and Deception: Impersonating authorized personnel or seemingly harmless individuals to gain trust.
4. Where Are Common Locations for Tailgating Incidents?
Tailgating is more prevalent in:
- Multitenant Buildings: High traffic makes it harder to identify and track unauthorized individuals.
- Companies with Lax Security Culture: Where employees lack cybersecurity awareness or don’t follow best practices.
5. What Are the Potential Dangers and Consequences of Tailgating?
Tailgating poses significant risks to organizations:
- Data Breaches: Exfiltration of sensitive information.
- Theft of Equipment: Stealing laptops or other valuable assets.
- Malware and Spyware Installation: Compromising devices with malicious software.
- System Disruption: Turning off critical systems or creating backdoors.
- Espionage: Installing cameras or listening devices for corporate or cyberespionage.
- Financial Loss: Stealing money, intellectual property, or client lists.
- Physical Damage: Vandalism or destruction of property.
6. Who Are the Typical Perpetrators of Tailgating?
Tailgaters can include:
- Disgruntled Former Employees
- Thieves
- Vandals
- Mischief Makers
- Anyone with a Grievance or Intent to Profit
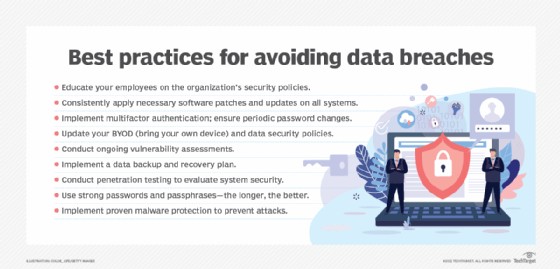
7. How Can Organizations Effectively Prevent Tailgating?
Organizations can implement several security measures:
- Electronic Access Doors: Install access control systems with swiftly closing doors.
- Revolving Doors: Use security revolving doors that detect tailgating attempts.
- Laser Sensors or Mantraps: Limit entry to one person at a time.
- Biometric Scanners: Use fingerprint, palm print, or retinal scanners for individual identification.
- Smart Cards: Customize smart cards for individual use with access control mechanisms.
- Photo IDs: Require employees to wear visible photo IDs and provide temporary badges for visitors.
- Video Surveillance: Install CCTV systems for 24/7 monitoring.
- Multifactor Authentication (MFA): Require multiple credentials for access, such as a card and a fingerprint.
- Human Security Guards: Train guards to question unfamiliar personnel and detain suspicious individuals.
8. What Role Does Employee Education Play in Preventing Tailgating?
Employee education is crucial:
- Awareness of Dangers: Educate employees about the risks of tailgating.
- Recognition of Attempts: Teach employees how to identify tailgating attempts.
- Preventive Actions: Train employees on how to resist tailgating and keep unauthorized individuals out.
- Promote a Security Culture: Foster a strong cybersecurity awareness culture throughout the organization.
9. What Security Best Practices Should Employees Follow to Avoid Tailgating?
Employees should:
- Never hold the door open for anyone.
- Always keep doors closed, especially to secure areas.
- Stop people from following them into restricted areas without proper badges.
- Verify the legitimacy of outsiders, such as repairmen or delivery persons.
- Direct unfamiliar people to the reception desk.
- Report suspicious activity to security guards.
- Inform the IT team if an electronic door malfunctions.
10. What Is the Key Difference Between Tailgating and Piggybacking?
While both are social engineering attacks, the key difference lies in consent:
- Tailgating: Occurs without the authorized person’s knowledge or permission.
- Piggybacking: Involves the authorized person knowingly granting access, often under false pretenses.
11. Electronic Access Control Systems to Prevent Tailgating
Electronic access control systems are a cornerstone of physical security, playing a vital role in preventing tailgating. These systems utilize technology to regulate and monitor entry into restricted areas, ensuring that only authorized personnel gain access. By implementing electronic access controls, organizations can significantly reduce the risk of unauthorized entry and enhance overall security.
How Electronic Access Control Works
Electronic access control systems employ various methods to verify the identity of individuals seeking entry. These methods can include:
- Keycards and Fobs: Employees are issued keycards or fobs that, when presented to a reader, grant access to authorized areas.
- Biometric Scanners: These scanners use unique biological traits, such as fingerprints, iris scans, or facial recognition, to verify identity.
- PIN Codes: Users enter a personal identification number (PIN) on a keypad to gain access.
- Mobile Credentials: Smartphones can be used as access credentials, communicating with readers via Bluetooth or Near Field Communication (NFC).
Once an individual’s identity is verified, the system unlocks the door or gate, allowing them to enter. The system also logs all access attempts, providing a valuable audit trail for security monitoring and investigations.
Benefits of Electronic Access Control
Electronic access control systems offer numerous benefits in preventing tailgating:
- Reduced Reliance on Human Vigilance: Automated systems minimize the potential for human error or carelessness in verifying identities.
- Enhanced Security: Multi-layered authentication methods, such as combining keycards with biometric scanners, make it more difficult for unauthorized individuals to gain access.
- Real-time Monitoring: Systems can provide real-time alerts when unauthorized access attempts are detected, allowing security personnel to respond quickly.
- Audit Trails: Detailed logs of access attempts provide valuable information for security investigations and compliance purposes.
- Integration with Other Security Systems: Electronic access control systems can be integrated with other security systems, such as video surveillance and alarm systems, for a comprehensive security solution.
Tips for Implementing Electronic Access Control
When implementing electronic access control systems, consider these tips:
- Choose the Right System: Select a system that meets your organization’s specific security needs and budget.
- Proper Installation: Ensure the system is installed correctly by qualified professionals.
- Regular Maintenance: Maintain the system regularly to ensure optimal performance.
- Employee Training: Train employees on how to use the system correctly and report any issues.
- Regular Audits: Conduct regular audits of the system to identify and address any vulnerabilities.
12. The Role of Security Guards in Preventing Tailgating
Security guards are a critical component of physical security, serving as the first line of defense against tailgating. Their presence and vigilance can deter potential intruders and ensure that only authorized personnel gain access to secured areas. By effectively performing their duties, security guards play a vital role in maintaining a safe and secure environment.
Responsibilities of Security Guards in Preventing Tailgating
Security guards have several key responsibilities in preventing tailgating:
- Monitoring Entrances: Guards should be stationed at entrances to observe individuals seeking entry.
- Verifying Identification: Guards should verify the identification of all individuals, ensuring they have proper authorization to enter.
- Questioning Suspicious Individuals: Guards should question individuals who appear suspicious or do not have proper identification.
- Enforcing Security Policies: Guards should enforce security policies, such as requiring employees to wear visible ID badges.
- Responding to Security Incidents: Guards should be trained to respond to security incidents, such as unauthorized entry attempts.
- Reporting Security Breaches: Guards should report any security breaches to the appropriate authorities.
Training and Skills for Security Guards
To effectively prevent tailgating, security guards should possess the following training and skills:
- Security Awareness: Guards should have a thorough understanding of security threats, including tailgating.
- Observation Skills: Guards should be able to observe and identify suspicious behavior.
- Communication Skills: Guards should be able to communicate effectively with individuals seeking entry and with their colleagues.
- Conflict Resolution Skills: Guards should be able to handle conflicts and de-escalate tense situations.
- Emergency Response Training: Guards should be trained to respond to emergencies, such as medical incidents or security breaches.
Tips for Security Guards in Preventing Tailgating
Security guards can follow these tips to effectively prevent tailgating:
- Be Visible and Approachable: A visible presence can deter potential intruders.
- Maintain a Professional Demeanor: A professional demeanor can command respect and discourage unauthorized entry attempts.
- Be Attentive: Pay close attention to individuals seeking entry and their behavior.
- Ask Questions: Don’t hesitate to ask questions to verify an individual’s identity and purpose.
- Trust Your Instincts: If something doesn’t feel right, investigate further.
- Follow Security Procedures: Adhere to established security procedures and protocols.
- Report Suspicious Activity: Report any suspicious activity to the appropriate authorities.
13. How Multifactor Authentication (MFA) Helps in Preventing Tailgating
Multifactor authentication (MFA) is a security measure that requires users to provide multiple verification factors to gain access to a system or area. This approach significantly enhances security by making it more difficult for unauthorized individuals to bypass access controls, including those attempting to tailgate. By implementing MFA, organizations can strengthen their defenses against a wide range of security threats.
How MFA Works
MFA combines two or more independent authentication factors, typically from the following categories:
- Something You Know: This includes passwords, PINs, or security questions.
- Something You Have: This includes access cards, security tokens, or smartphones.
- Something You Are: This includes biometric data, such as fingerprints, iris scans, or facial recognition.
For example, an employee might be required to present an access card (something they have) and enter a PIN (something they know) to enter a secure area. This approach ensures that even if one authentication factor is compromised, the unauthorized individual will still be unable to gain access without the other factor.
Benefits of MFA in Preventing Tailgating
MFA offers several benefits in preventing tailgating:
- Increased Security: MFA significantly increases the difficulty for unauthorized individuals to gain access, as they would need to compromise multiple authentication factors.
- Reduced Reliance on Single Factor Authentication: MFA reduces the reliance on single-factor authentication methods, such as passwords, which are more vulnerable to compromise.
- Enhanced Accountability: MFA can provide a more accurate audit trail of access attempts, making it easier to identify and investigate security breaches.
- Compliance Requirements: Many regulations and standards require MFA for sensitive data and systems.
Tips for Implementing MFA
When implementing MFA, consider these tips:
- Choose the Right Factors: Select authentication factors that are appropriate for your organization’s security needs and risk profile.
- User-Friendly Implementation: Implement MFA in a way that is user-friendly and does not create unnecessary friction for authorized users.
- Employee Training: Train employees on how to use MFA correctly and report any issues.
- Regular Audits: Conduct regular audits of the MFA system to identify and address any vulnerabilities.
- Consider Contextual Factors: Consider incorporating contextual factors, such as location and time of day, into the MFA process to further enhance security.
14. The Importance of a Strong Security Culture in Preventing Tailgating
A strong security culture is essential for preventing tailgating. It involves creating an environment where security awareness is ingrained in every employee’s mindset and actions. This culture emphasizes the importance of security protocols and encourages employees to take personal responsibility for protecting the organization’s assets.
Key Elements of a Strong Security Culture
A strong security culture encompasses the following key elements:
- Executive Leadership Support: Senior management must champion security and demonstrate their commitment through resource allocation and policy enforcement.
- Employee Education and Training: Regular training programs should educate employees about security threats, policies, and best practices.
- Clear Security Policies: Comprehensive and well-defined security policies should be readily accessible to all employees.
- Open Communication: Encourage employees to report security concerns or suspicious activity without fear of reprisal.
- Positive Reinforcement: Recognize and reward employees who demonstrate good security practices.
- Continuous Improvement: Regularly evaluate and update security measures to address evolving threats and vulnerabilities.
How a Strong Security Culture Prevents Tailgating
A strong security culture directly contributes to preventing tailgating by:
- Raising Awareness: Employees are more likely to be aware of the risks of tailgating and the importance of following security protocols.
- Promoting Vigilance: Employees are encouraged to be vigilant and report any suspicious activity.
- Encouraging Responsibility: Employees take personal responsibility for protecting the organization’s assets and preventing unauthorized access.
- Fostering Compliance: Employees are more likely to comply with security policies and procedures.
- Creating a Deterrent: A strong security culture can deter potential intruders from attempting to tailgate.
Tips for Building a Strong Security Culture
Organizations can take the following steps to build a strong security culture:
- Start at the Top: Executive leadership must champion security and set the tone for the organization.
- Communicate Regularly: Communicate security messages frequently and consistently through various channels.
- Make Security Relevant: Tailor security training to specific job roles and responsibilities.
- Engage Employees: Use interactive training methods, such as simulations and gamification, to engage employees and make learning fun.
- Measure and Track Progress: Track key metrics, such as security awareness scores and incident reports, to measure the effectiveness of security culture initiatives.
- Celebrate Successes: Recognize and reward employees who demonstrate good security practices.
15. Emerging Technologies for Preventing Tailgating
As security threats evolve, new technologies are emerging to combat tailgating. These technologies offer advanced capabilities for detecting and preventing unauthorized entry, enhancing overall physical security. By embracing these innovations, organizations can stay ahead of potential intruders and maintain a secure environment.
Examples of Emerging Technologies
Here are some examples of emerging technologies for preventing tailgating:
- AI-Powered Video Surveillance: Artificial intelligence (AI) can analyze video footage in real-time to detect suspicious behavior, such as individuals following too closely behind authorized personnel.
- 3D Sensors: Three-dimensional (3D) sensors can accurately measure the depth and shape of objects, allowing them to distinguish between individuals and prevent tailgating attempts.
- Millimeter Wave Radar: This technology can penetrate clothing and other materials to detect hidden objects, such as weapons or explosives.
- Behavioral Analytics: By analyzing patterns of behavior, these systems can identify anomalies that may indicate tailgating attempts.
- Smart Locks: Smart locks can be integrated with access control systems to provide remote locking and unlocking capabilities, as well as real-time alerts for unauthorized access attempts.
Benefits of Emerging Technologies
These emerging technologies offer several benefits in preventing tailgating:
- Enhanced Detection Capabilities: They can detect tailgating attempts more accurately and reliably than traditional methods.
- Real-Time Alerts: They can provide real-time alerts to security personnel, allowing them to respond quickly to potential breaches.
- Automated Response: Some systems can automatically lock doors or trigger alarms when tailgating is detected.
- Improved Efficiency: They can automate security tasks, freeing up security personnel to focus on other priorities.
Considerations for Implementing Emerging Technologies
When implementing emerging technologies for preventing tailgating, consider the following:
- Cost: Emerging technologies can be more expensive than traditional security measures.
- Integration: Ensure that the new technologies can be integrated with existing security systems.
- Training: Provide adequate training to security personnel on how to use and maintain the new technologies.
- Privacy Concerns: Address any privacy concerns related to the use of these technologies.
- Scalability: Choose technologies that can be scaled to meet the organization’s future security needs.
Tailgating is a serious security concern that can have significant consequences for organizations. By understanding the methods used in tailgating attacks, implementing appropriate security measures, and fostering a strong security culture, organizations can effectively prevent tailgating and protect their assets.
Do you have any security questions or concerns? Visit what.edu.vn for free answers and expert advice. Our team is ready to help you protect your organization from all types of security threats. Contact us at 888 Question City Plaza, Seattle, WA 98101, United States, or via WhatsApp at +1 (206) 555-7890. We are available 24/7.